Big $$ And Personal Privacy – Organizations And The Cost Of Email Phishing
January 6, 2023
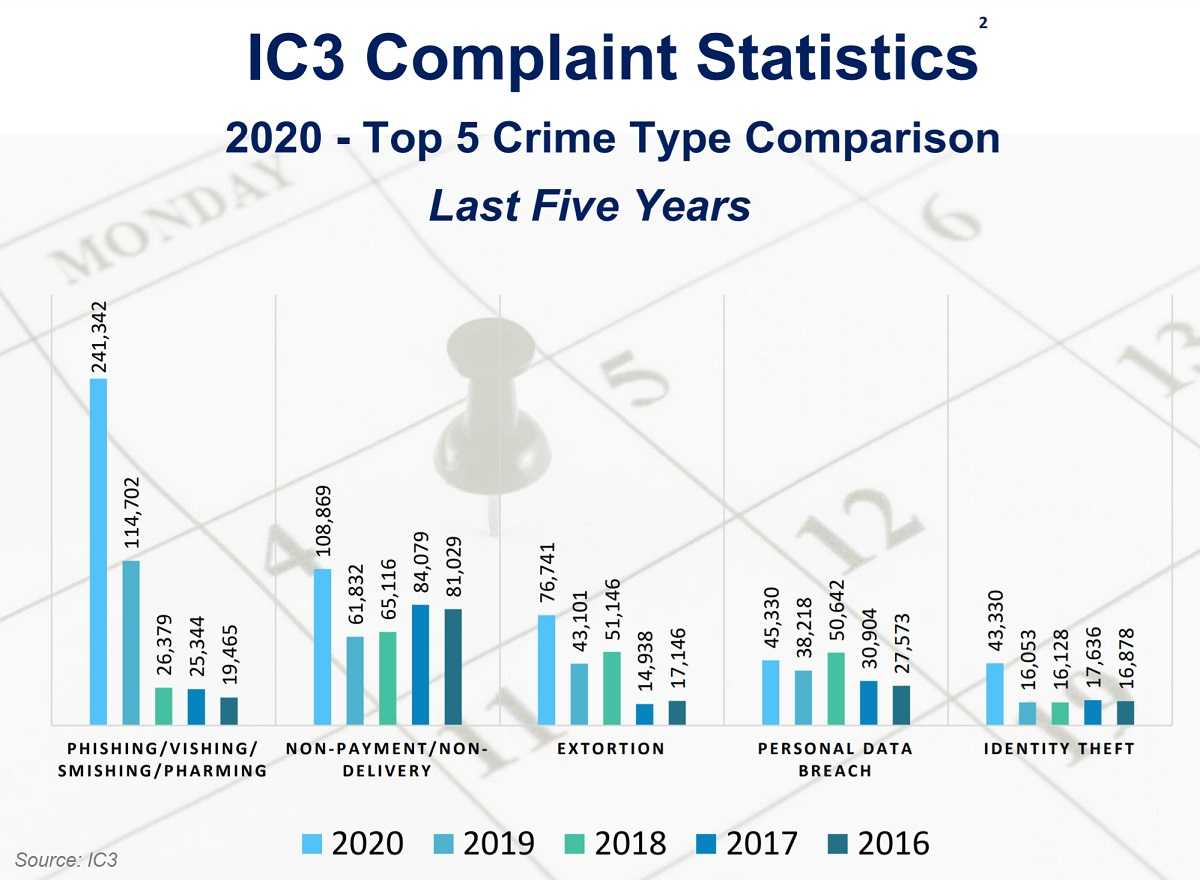
The price tag of email phishing attacks is growing, and it’s not just money that’s vulnerable. Employees and even children learning with remote set-ups can inadvertently lose their privacy to hackers, adding to the personal cost of these attacks. The FBI’s 2020 IC3 (Internet Crime Complaint Center) report found phishing attacks are some of the most prevalent cybercrimes, with organizations in the U.S. losing $54 million to this attack vector that year. The report also finds that BEC (business email compromise) is the costliest type of email phishing, with the IC3 finding close to $1.8 billion in losses to U.S. businesses. With a reported 3 billion emails sent by cybercriminals every day, it’s no wonder these attacks are so pervasive and successful.
A study by Proofpoint finds the main consequences of phishing attacks to organizations are lost data (60%), compromised accounts or credentials (52%), ransomware (47%) and malware infections (29%.) A Verizon report finds the most common types of data compromise are credentials like passwords and usernames, personally identifiable information (PII) like phone numbers and physical addresses, a company’s internal data, and medical and banking information. Aside from businesses, education is also a prime target for phishing attacks. Hackers know how especially vulnerable and ill-prepared many of these organizations are to fight-off cybercrimes.
The non-profit K-12 Security Information Exchange reports the school district comptroller in Del Rio, TX caught in an email phishing attack sent over $2 million to a hacker. In Broward County, FL, school district officials refused to pay a ransomware demand of $40 million. Their refusal to pay, according to local reports, meant hordes of stolen files were publicly published, including those with confidential information. Spear phishing, a highly targeted email, costs a median $2 million per incident since 2016, with a record $9.8 million stolen last year from a lone school district.
Listed below are everyday precautions remote users can take to keep their PII other data in their environment safer.
- Share information carefully. Before sharing personal information, consider where it will end up and who may be viewing it. That’s especially true for video conferencing apps like Zoom and other collaboration platforms, where only the needed information should be visible. Remember, device cameras are a gateway for intruders and security incidents.
- Have a vetting process. Before a remote class or meeting starts, consider a waiting room to verify participants arriving are who they say they are. Also, consider giving participants an option to participate only by audio if they have privacy concerns.
- Require multi-factor authentication (MFA) for business related and learning apps when possible. It’s an easy and effective way to keep hackers away from remote use vulnerabilities.