Increasing Ransomware Attacks By State-Backed North Korean Hackers
May 2, 2023
State-backed North Korean hackers have long been implicated in ransomware attacks targeting healthcare facilities and critical infrastructure. South Korean and U.S. cybersecurity and intelligence agencies have jointly issued a statement claiming the monies generated by this illegal activity by North Korea are used to fund illicit activities and further the objectives of North Korea. And a recent warning has been issued that claims U.S. government departments are actively in the hacker’s bullseye.
Cybersecurity experts believe that ransomware efforts are currently focused on the information networks of the Department of Defense and the Defense Industrial Base member networks. Ransomware is executed demanding cryptocurrency as payment or they will not decrypt the data.
Threat actors based in North Korea are often singled out as a clear and present danger to information networks in the United States. North Korean Hackers assumed global prominence in 2017 due to the WannaCry ransomware attacks that infected hundreds of thousands of machines in over 150 countries across the globe.
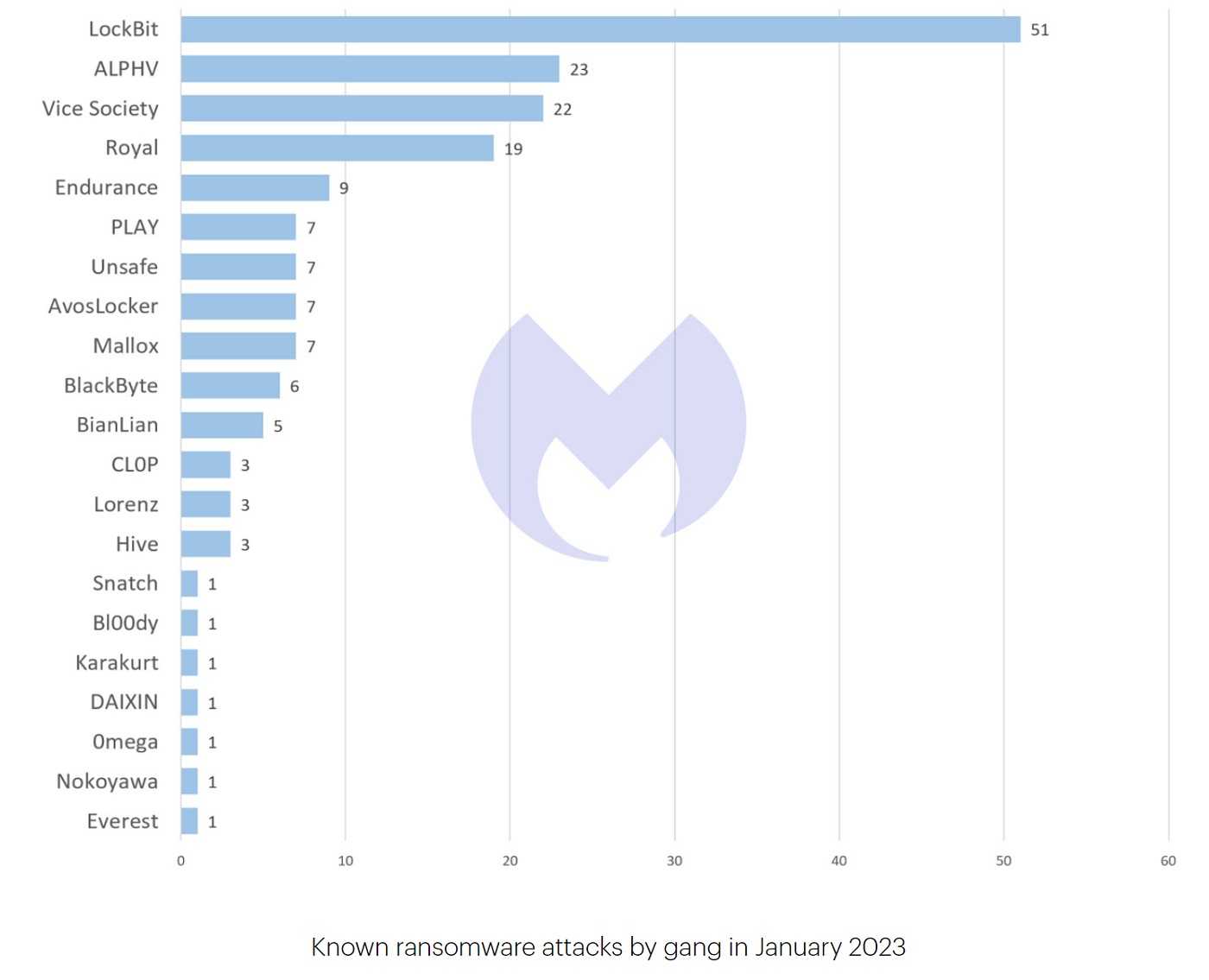
This hacking group was responsible for the theft of over $1 billion in 2022, and the attacks are increasing in frequency and complexity. The attacks exploit security flaws in TerraMaster NAS appliances, Apache Log4j, and SonicWall. The attacks then progress to the launch of ransomware. Not only do these threat actors develop their own ransomware tools, but they also have been known to use widely available third-party tools such as Jigsaw, DeadBolt, BitLocker, ech0raix, and YourRansom to encrypt files.
Regardless of the industry, expert cybersecurity agencies advise all organizations to implement the concepts of “least privilege.” If access isn’t needed to do the work, it shouldn’t be granted. Make sure that multi-layer segmentation of the network is in place. This limits access to any unauthorized party, should one segment be breached. The functionality of unnecessary network device management interfaces should be curtailed as well. In addition, scheduling regular data backups are both essential and protective measures. Be sure to keep the backups separate from the operational network and if possible, far from Internet reach.
As always, implemented an ongoing phishing awareness program. Threats are continually changing. The staff’s knowledge of them should be continual too.