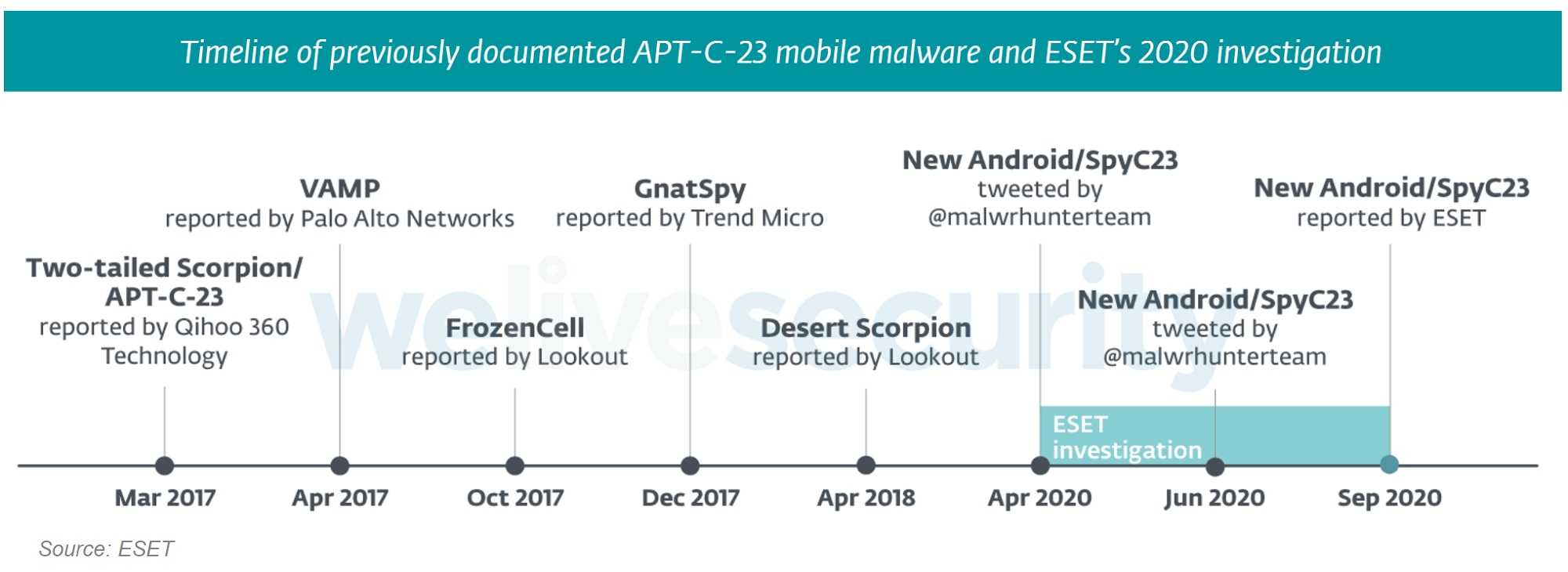
No one wants to think their smartphone is also a spying device, but a recent discovery found a new Android spyware is finding a home on mobile devices. This new spyware is the latest version since first being detected in 2017, and it has gone through many improvements since then. The spyware, called Android/SpyC23.A and the hacking group behind it, have a history of using surveillance malware and both are well-known to the cybersecurity community worldwide. The spy group behind the threat, APT-C-23, is known for spying efforts in the Middle East and experts believe it’s just a matter of time before it’s unleashed in the US and other locations.
When compared to its 2017 version, this latest model has extended spying functions that earned it the name “surveillanceware” for its cutting-edge espionage ability. The original surveillance functions of Android/SpyC23.A were limited to phone call and screen recording, reading notifications from messaging apps, and the ability to dismiss notifications from built-in Android security apps. Recently, improvements to the original spyware version have changed significantly.

According to security firm ESET, this year’s model added more stealth functions like stealing contacts, call logs, messages, location, photos, and other sensitive data. Armed with extensive personal information, any number of malware attacks can sprout when exposed to bad actors. Also, crimes like identity theft and blackmail are predictable when criminals have an abundance of a victim’s PII (personally identifiable information).
Another revelation about this latest version is that the spyware is distributed through a bogus Android app store that uses well-known, popular messaging apps as a lure. Experts note a fake Android app store called “DigitalApps” has been used to promote three messaging apps intentionally infected with the spyware. When a user downloads Telegram, Threema, or weMessage, the spyware gets unleashed on a mobile device and all bets are off where privacy is concerned.
Now that we know more about the spyware Android/SpyC23.A and how it’s distributed, revisiting app security measures can help prevent this spyware and other malware from taking hold of a device.
App Do’s and Don'ts
 Always download apps from the official Google Play or Apple App stores. “Sideloading” apps from unofficial, third-party websites is very risky business and should always be avoided. The official stores scan for malware, but “unofficial” sites for sideloading apps are not so diligent. As we also see from the DigitalApps store, those apps that are knowingly infected are promoted and downloaded.
Always download apps from the official Google Play or Apple App stores. “Sideloading” apps from unofficial, third-party websites is very risky business and should always be avoided. The official stores scan for malware, but “unofficial” sites for sideloading apps are not so diligent. As we also see from the DigitalApps store, those apps that are knowingly infected are promoted and downloaded.
Before installation, reading app reviews can prevent getting stuck with problematic apps. Knowing negative issues ahead of time can change a user’s decision to download or not.
Pay attention to permission requests while downloading an app, and keep permissions limited to the lowest levels of access. If there’s a request for administrative access, deny it. No app needs that level of access and agreeing to it gives bad actors the green light to overtake a device.