It’s not the game many of us played as kids, but it is a distorted take on the same idea. Man-in-the-middle (MitM) cyberattacks do put someone in the middle of two sides, but that someone is a cybercriminal. And those on either side are clueless victims. In reality, MitM attacks are anything but a game.
How MitM Attacks Work
The goal of MitM attacks is making sure both sides believe they’re communicating directly with each other. That way, the hacker in the middle inserts themself into the conversation, “eavesdropping” and even manipulating what’s being communicated back and forth. A typical MitM attack can disrupt operations, intercept usernames and passwords, emails, banking, and other financial details. Below is the way MitM attacks play out, including ways to avoid being caught up in these crimes.
The MitM accesses networks, routers, and Wi-Fi connections, inserting themself into the middle of the two-way communication. Then, the MitM impersonates both people in the conversation, having them believe they’re talking directly with each other. While communicating back and forth, a MitM intercepts their messages. Hackers can alter them or insert their own messages and even inject malware, all with the goal of stealing sensitive data.
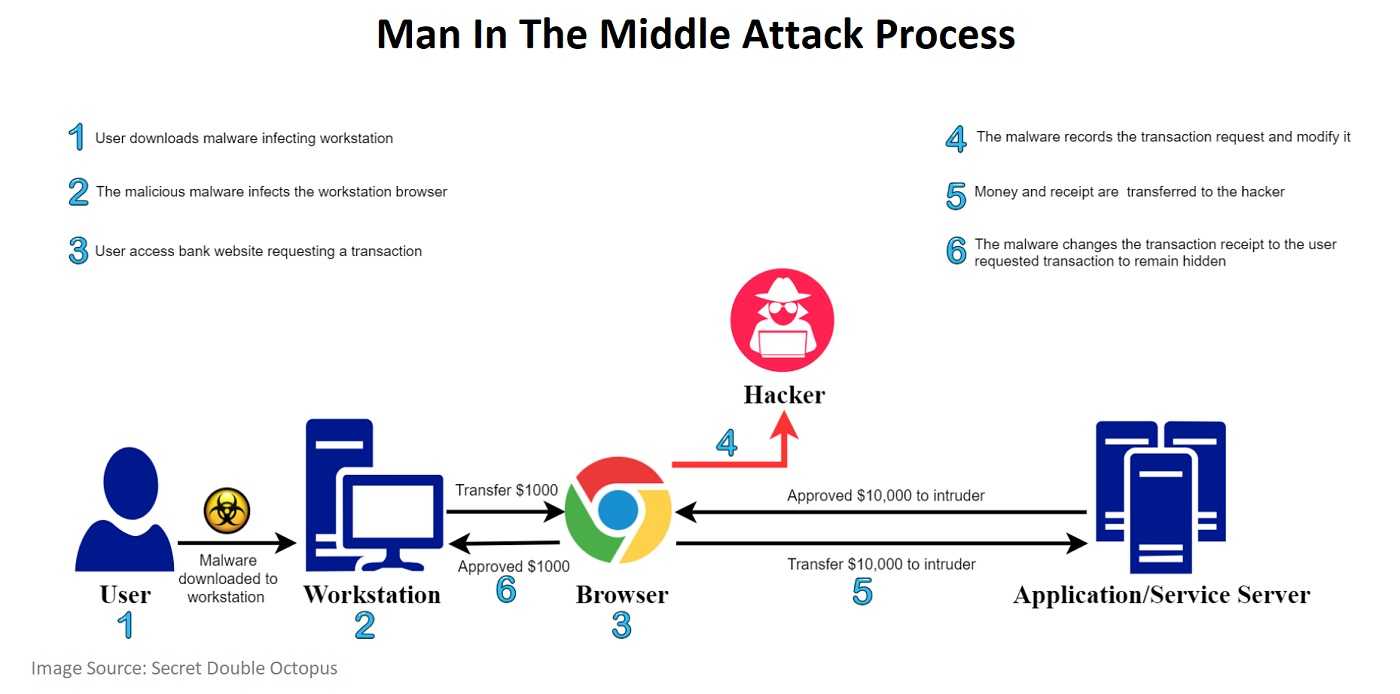
Avoiding MitM Attacks
Use caution while using public Wi-Fi as Information is easily intercepted by others. Consider using a VPN (Virtual Private Network) that encrypts internet connections and messages so they can’t be read by attackers.
Check website HTTPS, shown by a padlock icon to the far left of the web address/URL. The HTTPS encrypts information between the website and your browser, making it difficult for bad actors to change, intercept, or decipher it. While not 100% secure, it’s one indicator that the website is safe.
Always use two-factor authentication (2FA) when available. 2FA is an additional layer of identity authentication sent during login as a numerical code. The 2FA code prevents an attacker from logging into an account even if they have the password. For more security, use a hardware “key” or an authenticator app.
Keep all software updated, including browsers, programs, apps, and security. Updates frequently include bug fixes and improvements to device security. Turning on automatic updates can take some of the pressure off having to remember to do it manually.