Study Finds 90% Of Excel 4.0 Macros Distribute Malware
May 4, 2023
Since 1992, Excel 4.0 (XLM) macros are a scripting language that Microsoft Office still supports today. Using outdated technology is enough to welcome malicious actors interested in distributing malware through the legacy macro. A study by ReversingLabs finds 90% of the XLM macros they found are still in use and are likely malicious. XLMs give bad actors easy ways to access and abuse essential functions within a system. Many businesses still use XLM macro documents, and as a result, security issues are created. Security measures have a difficult time detecting macro malware in a system. With XLM still being used in businesses today, blocking XLM macros isn’t currently an option.

A macro is an action or group of actions that help automate repetitive tasks. Creating a macro involves recording mouse clicks and keystrokes that can be used as many times as needed for the desired results. It’s easy to forget this technology still exists today, especially since Microsoft created a more advanced VBA (Visual Basic for Applications) macro just one year after XLM came to fruition.
Macro Mania
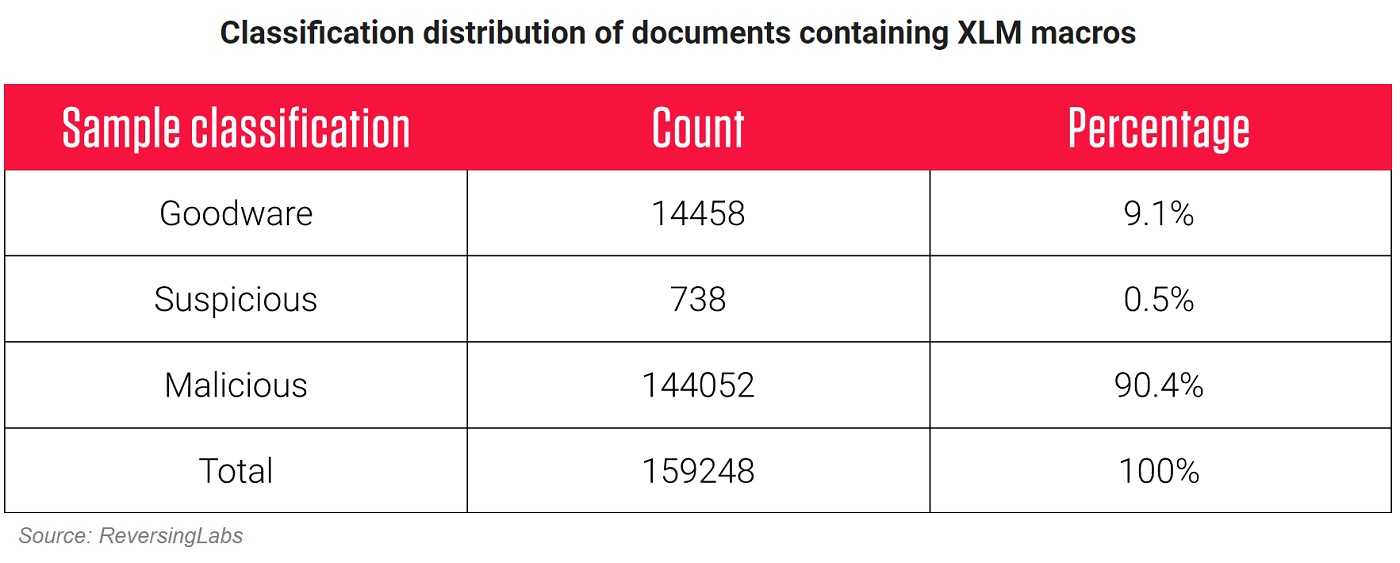
For nearly six months, a ReversingLabs study collected all Excel documents appearing for the first time in their TitaniumCloud. The documents were analyzed by the company, finding almost 160,000 still use XLM macros. TitaniumCloud identified more than 90% of those documents were classified as malicious or suspicious. So, if you have a document using XLM macros, it’s a safe bet the macro is malicious.
Disable or Enable Macros
 The security issues surrounding XLM today are the very reasons cybercriminals make it a macro of choice to deliver their malware. Stopping these attacks from creeping into a system isn’t a complicated process, rather, it can be as easy as disabling all macros by default – which security experts strongly recommend. In a support document on using XLM, Microsoft warns that if all macros are enabled it can cause “potentially dangerous code” to run.
The security issues surrounding XLM today are the very reasons cybercriminals make it a macro of choice to deliver their malware. Stopping these attacks from creeping into a system isn’t a complicated process, rather, it can be as easy as disabling all macros by default – which security experts strongly recommend. In a support document on using XLM, Microsoft warns that if all macros are enabled it can cause “potentially dangerous code” to run.
Disabling macros is as easy as changing the security setting to “disable.” Microsoft now automatically disables macros by default, but that wasn’t the case in earlier version of the software. If you get a message saying a macro needs enabling to run a program, the next step should be putting the macro under a microscope. Check with your IT department before enabling the macro, including the source of the document. Hackers use spear phishing emails to target staffers with an attached Excel or other program that’s hiding malicious macros, or via a download link in the email. It always pays to run an email through phishing red flags before acting on it.
According to Reversing Labs, when it comes to using XLM macros “…some things should have a life expectancy…the cost of maintaining 30 year old macros should be weighed against the security risks using such outdated technology brings.”