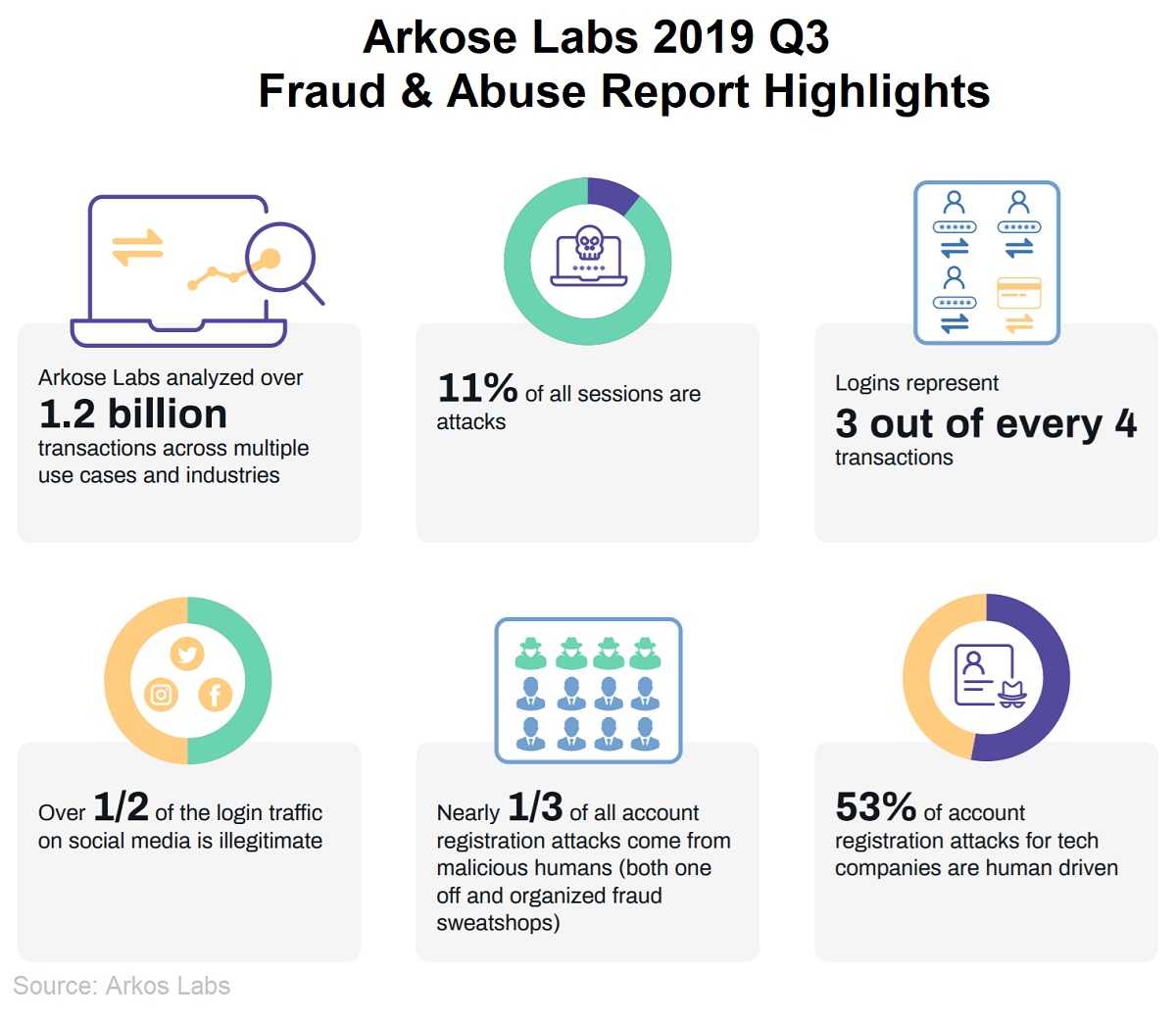
Social media attacks are a favorite of those pesky cybercriminals. One might wonder why. Well, it’s because it’s easy pickin's going for those accounts. Researchers at Arkose Labs found that of 1.2 billion social media interactions, 53% of the logins were fraudulent and 25% of new accounts were phony. Millions of people use one form of social media or another, whether it’s Facebook, Instagram, Snapchat, LinkedIn, or something else. That leaves a barrel full of phish used for targets for hackers and scammers.
These are the ways social medial is used to perpetrate top scams and crimes on social media, in no particular order:
URL Abuse and propagation attacks. These types of scams can include typosquatting as well as flat out theft or impersonation of legitimate web addresses. It also includes using short URLs (bitly and tinyurl, for example). Typosquatting takes advantage of a user’s typos while other domain names are also mimicked in such a way it is difficult tell if they are real or not. In some case, the domain is taken over or the criminal puts up a façade over the actual site with intent to steal credentials. Short URLs mask a true URL so it is difficult to tell what the legitimate one is.
 Always recheck the URL or web address before hitting that < return> or < enter> key to be sure you are going to the correct website. Bookmark frequently used ones and don’t click on links that are masked using the short URL.
Always recheck the URL or web address before hitting that < return> or < enter> key to be sure you are going to the correct website. Bookmark frequently used ones and don’t click on links that are masked using the short URL.
Social engineering and intelligence gathering. Whatever you post on any type of social media is fair game for cybercriminals to use against you or others. It’s not uncommon for them to peruse social media sites, gather information, and create very specialized and targeted attacks against victims.
Take care when posting information on social media, especially on business networking sites such as LinkedIn. What you post there can be used against you personally or professionally putting both you and your organization at risk for various scams, such as business email compromise (BEC) and wire fraud scams.
Identity theft and credential theft. Social media provides scammers with an abundance of information for phishing attacks. Often, they create false identities and prey on their victims on the various social media platforms. They collect data and use it in targeted attacks to get login credentials and other personally identifying information (PII).
Romance and Nigerian prince (419) scams. Scammers peruse social media to find victims for romance, 419, and other types of online scams. These allow the scammers to become an alternate identity and take advantage of the emotions of the victims. In romance scams, they will often pretend to have romantic feelings in an attempt to get the victim to send money. In the 419 scams, they pretend to be a prince or other royalty or government official who is in trouble of some sort and purports to need help.
If you have not met someone personally, don’t be tempted to give them money or gift cards. Always be certain you can trust people to whom you give money and never give out login credentials to anyone for any account.
Data dumps. These happen when an organization’s network is breached and the data contained within it is stolen and “dumped” somewhere for later use or to be sold on the dark web. The information kept within our social media accounts is valuable to hackers.
Protect login credentials and always use a unique password for every online account. Limit what information you post on social media, especially business-related ones. This information can be used against you and your organization. If you are the victim of a data breach, immediately change the password for the affected account.
Always use those cybersmarts and don’t click links or attachments from unknown persons or those that you are not expecting, no matter how you receive them.