Over the years, gift cards have become an enormous “go to” way of giving. Mageplaza found the purchase of gift cards this year will reach nearly $450 billion globally. And like many things involving monetary value and being human, cyber-scammers are exploiting gift cards for profit. They’re now combining gift card fraud with the world’s most lucrative cybercrime, business email compromise (BEC) attacks.
Typical BEC attacks target organization employees with emails appearing to be from a C-level or other high-ranking company executive. The emails often request urgent wire transfers and provide the account number for the transaction. The end result? The employee unknowingly sends funds to the scammer’s account. The exec has no idea about the transfer, and maybe worse, finds the crime done in their name.
BECs Adapt and Trend
According to researchers at Cofense, organizations are getting hip to more traditional BEC tricks and have bolstered protections against them. As a result, fraudsters needed a new lure and turned their attention to gift cards. Their cash-outs are hard to track, providing payoffs and anonymity for the criminals.
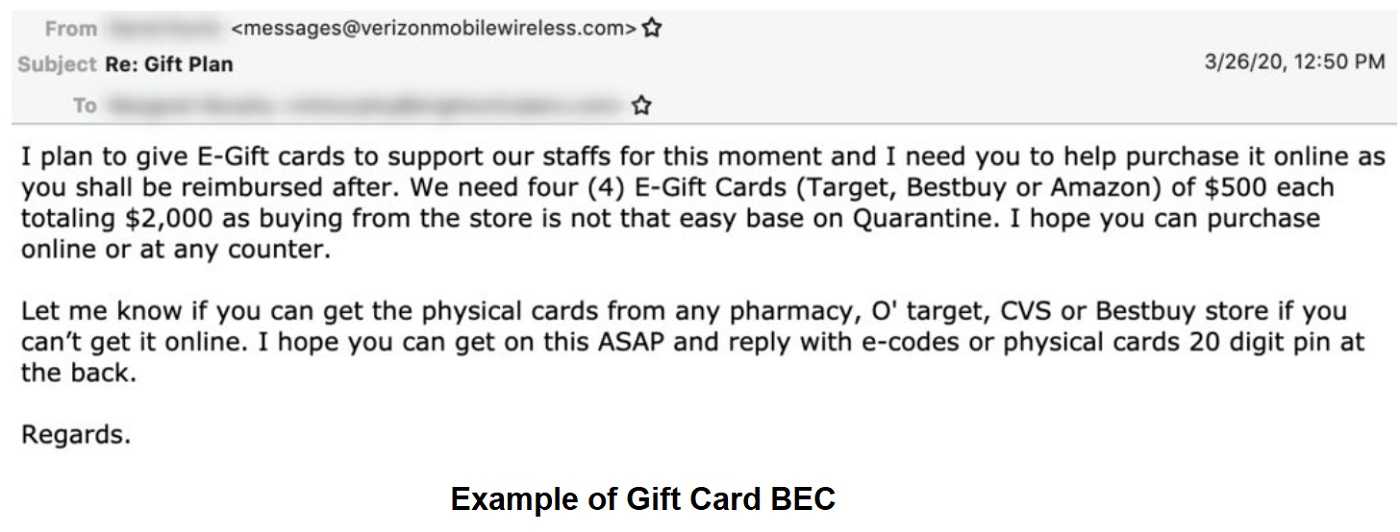
Cofense learned most scammers go for a quick, same-day turnaround to avoid the 72-hour anti-money laundering (AML) “safety window” for some cases. They sell the ill-gotten cards locally at about a 50% discount or unload them online at exchanges for 80-85% of their value, often selling them for payments in cryptocurrency.
FYI…scammers are picky about the gift cards they steal. They prefer amounts from $100-$500, specifically from stores as opposed to those from financial companies like Visa and American Express.
From Wire Transfers to Gift Cards
Cofense found adapting BECs from wire transfers to gift cards is a seamless transition. Instead of directing an employee to make financial transfers into an account setup for the BEC, the scammer emails the employee, asking if they can “help out” by purchasing gift cards for them.
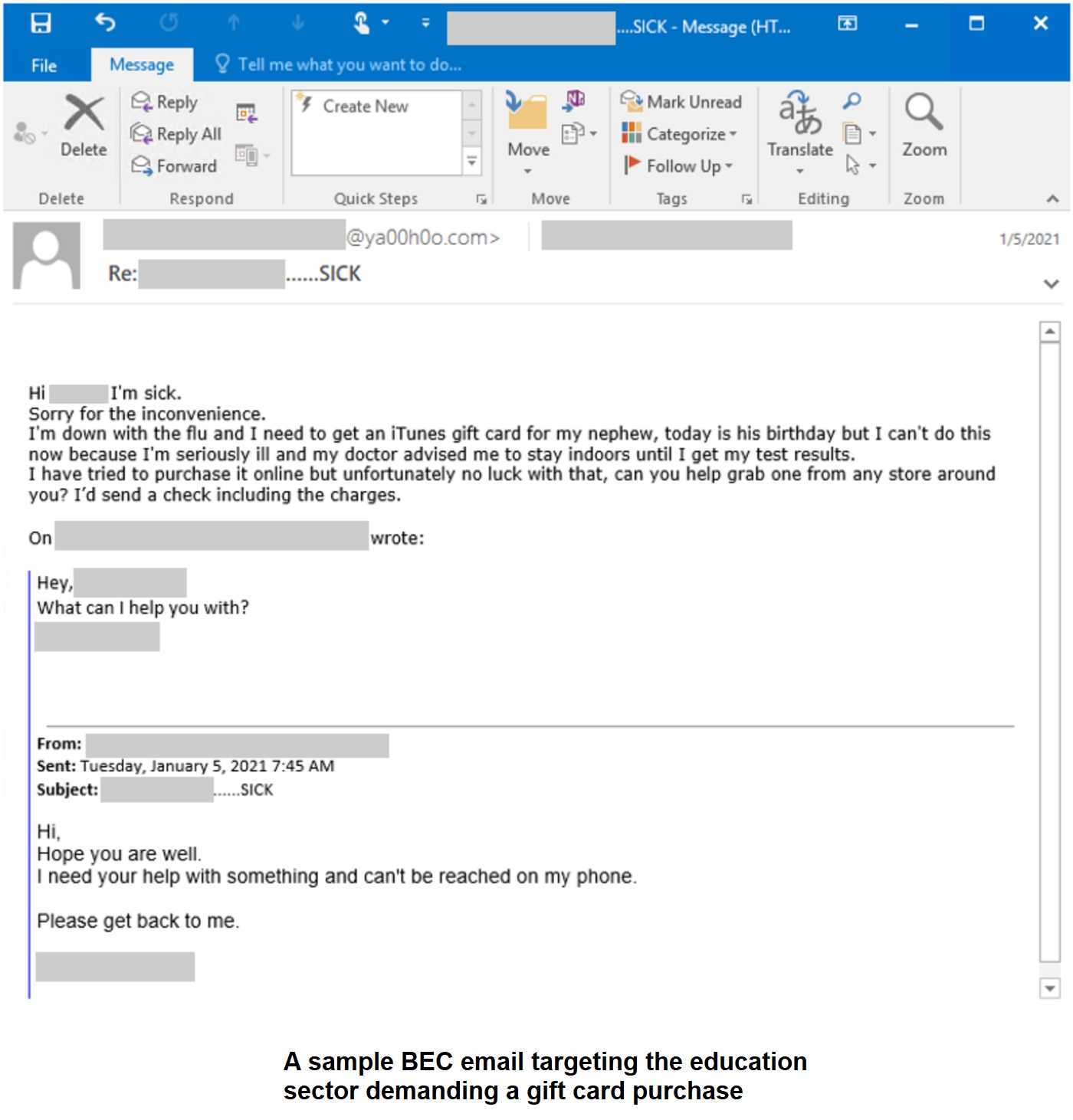
The email lures, also the reasons they give for needing the cards, range from employee holiday or birthday gifts, a “Thank You” for a client, and anything else sounding plausible. Once on the hook, the scammer (posing as the executive) has the victim scratch-off the card code and send pictures of the cards to them. At that point, the dirty deed is as good as done.
Phishing Successfully
Scammers get a lot of the information they need to impersonate a C-Level from the internet. LinkedIn is a treasure-trove of information for them. Specific details such as company names, titles, contact information, and a lot more are readily available. Contacts of those people are “linked” and easy enough to find. That information alone can make a spoofed email message easy for a scammer. So, everyone should limit what information is made available on social media or anywhere on the internet—even on the company website. The more information listed there, the more realistic a scammer can make an email with the goal of a BEC payout.
Policies should be in place to ensure wire transfers don’t go out to thieves. And now, a policy may need to be added to never pay for anything in gift cards. Keeping up with the latest, trending cybercrimes isn’t easy. But those who run a business should make it their business to know about cyberthreats like BECs; and gift card scams are just the latest reason why.