This latest crypto crime uses phishing and a malicious, fake Zoom link to steal cryptocurrency. With just one click, unsuspecting targets find their crypto accounts drained by a devious cyberattack. Here’s more of what you need to know about this new and sophisticated crime.
Opportunity Strikes
This scam uses a socially engineered approach by targeting specific “high value” individuals. Phishing is the first move, offering victims a totally bogus opportunity that sounds too good to pass up. The scammer uses high pressure tactics, insisting they meet on Zoom to seal the deal. Agreeing to the Zoom meeting turns this lure into a crime.
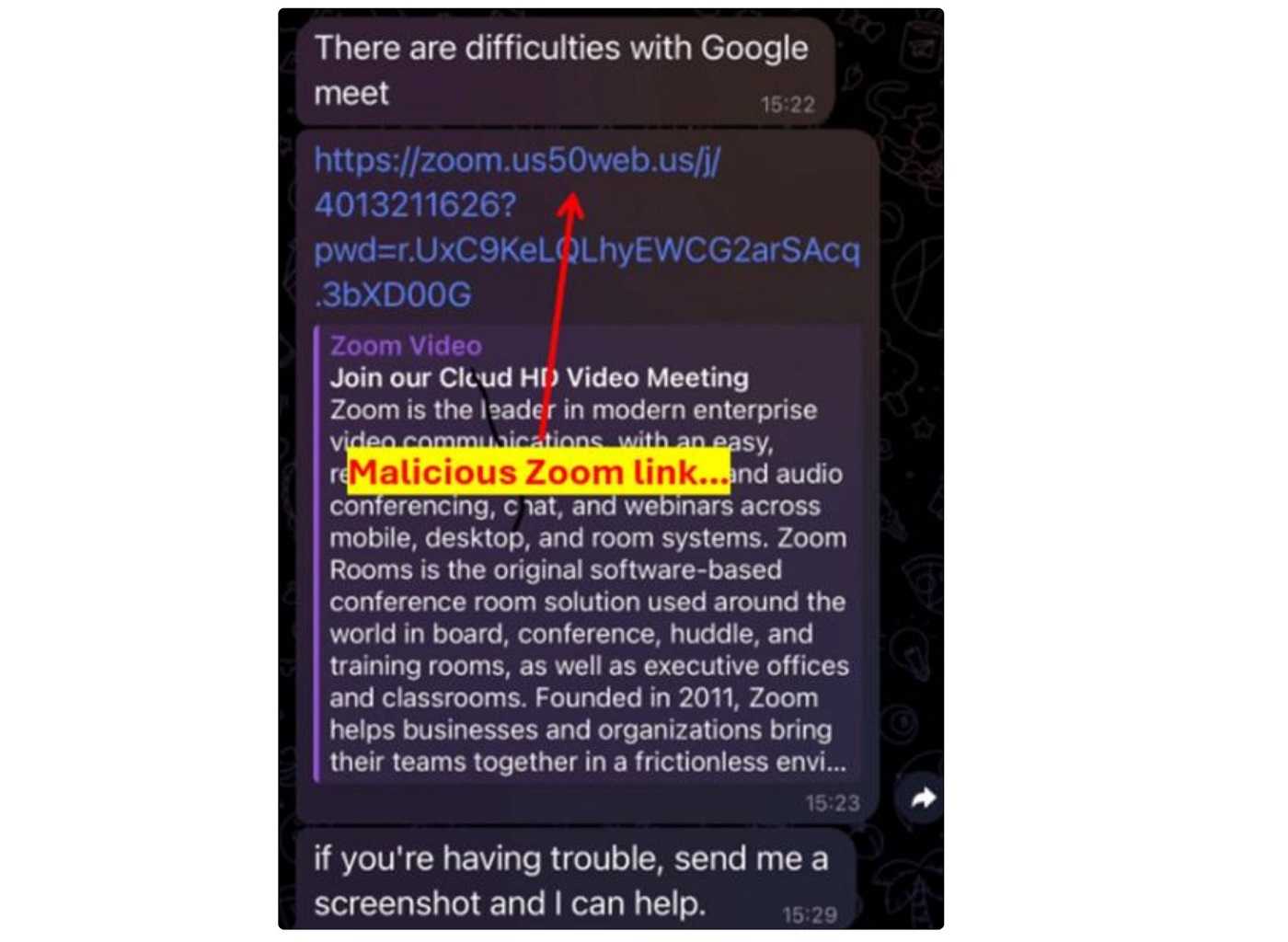
The attacker includes a bogus Zoom URL link for the meeting and the victim has no clue it’s full of malware. Once clicked, it shows a loading and other screens that look Zoom-legitimate. But what’s really loading is malware concealed as the Zoom installer. While waiting for the Zoom link to finish installing, the malware starts stealing information from the victim’s device.
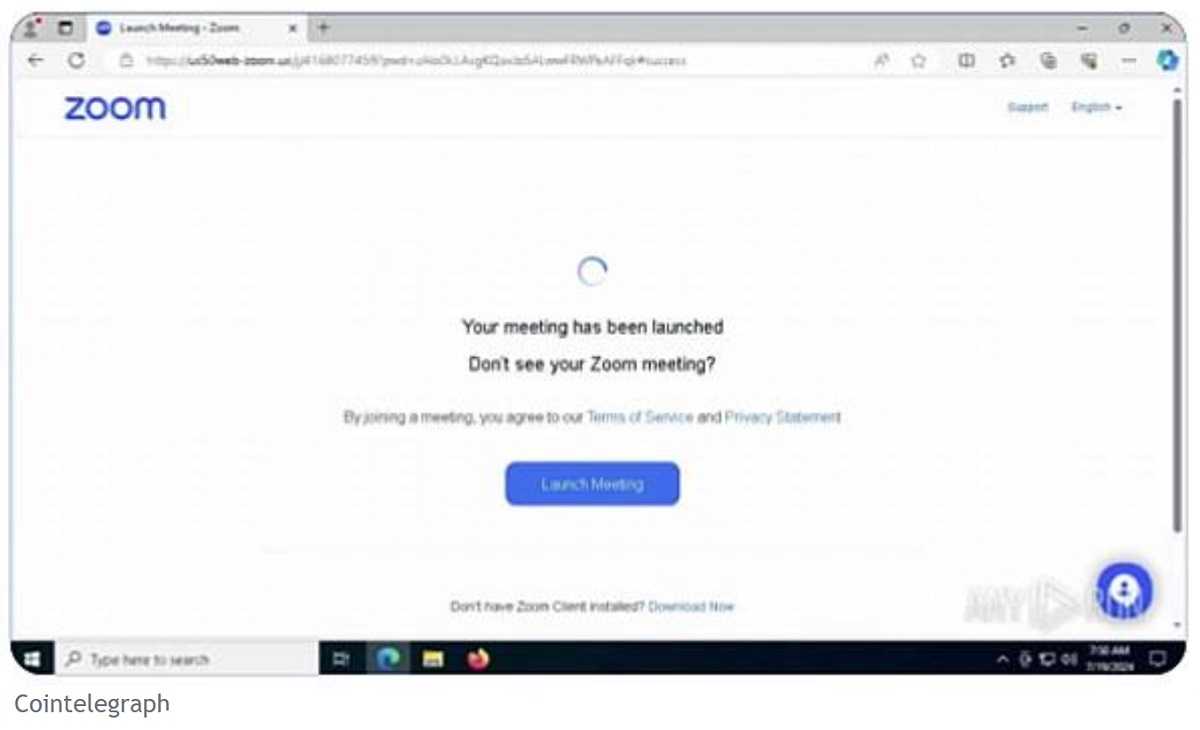
There’s no limit to what this malware steals, including crypto accounts, PII, and whatever else it can. Since the attacker encrypts the malware first, it’s even likely to get past anti-virus protection. So, what can you do to avoid becoming the next Zoom victim?
Safe Zoom-ing
Clicking on links sent by others is never a cyber-smart idea, especially if you don’t know or trust the person sending it. If you already have Zoom installed, you never need to reinstall it, especially just to have a meeting. In reality, you can use Zoom directly from your browser without installing it at all. So, if someone tells you that you absolutely MUST install it, consider it a big old red flag.
Remember that if an offer or “deal” sounds too good to be true, consider it too good to be true and opt out of participating.
Like most cybercrimes today, they keep rising to new levels of success. Using Zoom to pull-off this scam is new, but since it works well, we can plan on seeing more of it. The next time someone sends you a Zoom link for any reason, remember, one click is all it takes to zoom in on a lot of trouble.
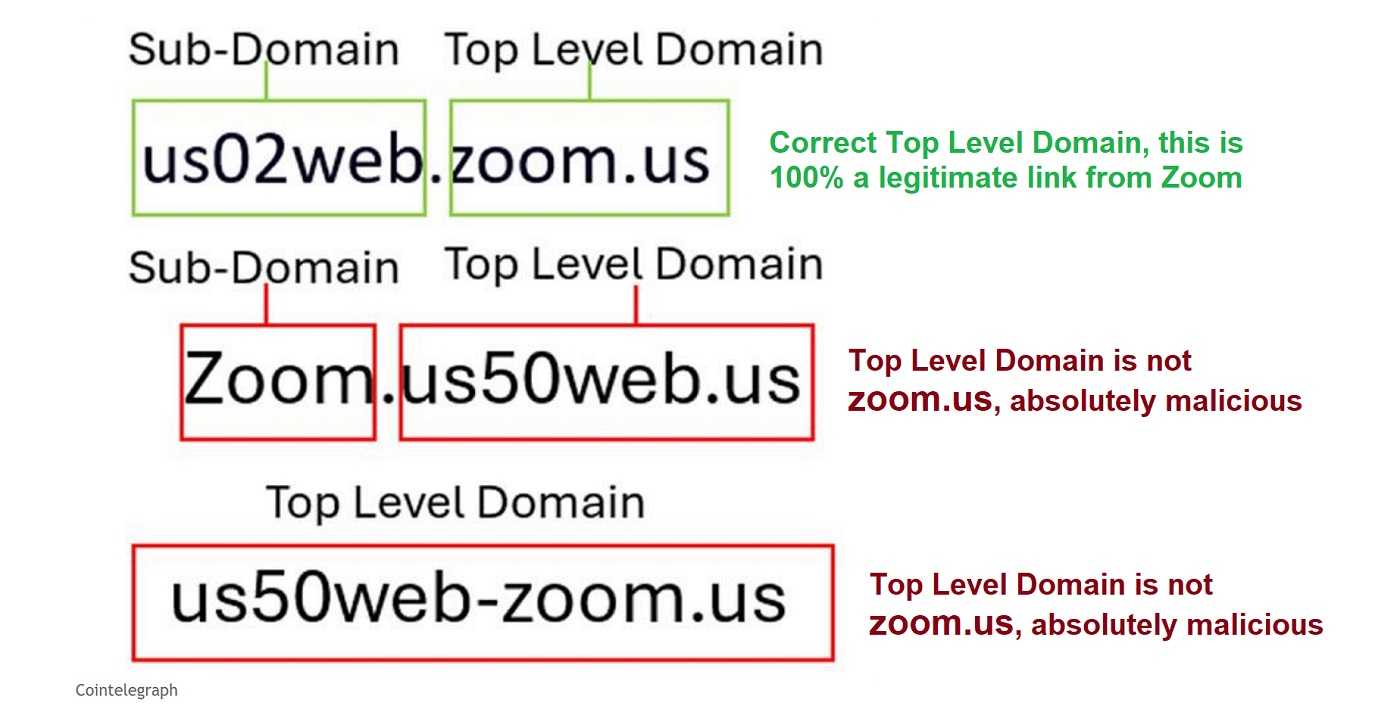
Always examine the domain of any link. If the Top Level Domain is not the official domain of the company represented in the link, it more than likely is a malicious link.