It’s no secret that in the U.S., cybercriminals placed a bullseye on healthcare systems and the sensitive patient data they hold. A recent study shows over a five-year period, nearly 42 million patients had their PHI (Protected Health Information) compromised by ransomware attacks. This previously unprecedented number of victims makes PHI security more important now than ever before.
From 2016-2021, the Journal of the American Medical Association (JAMA) studied the explosion in healthcare ransomware attacks. They found 374 reported attacks exposed the record-breaking 42 million victims and their PHI records. JAMA believes these attacks are likely underreported, making the true number of victims and PHI exposure even higher. Stolen PHI can be sold on dark web forums, leading to further cybercrimes like identity theft and account takeovers.
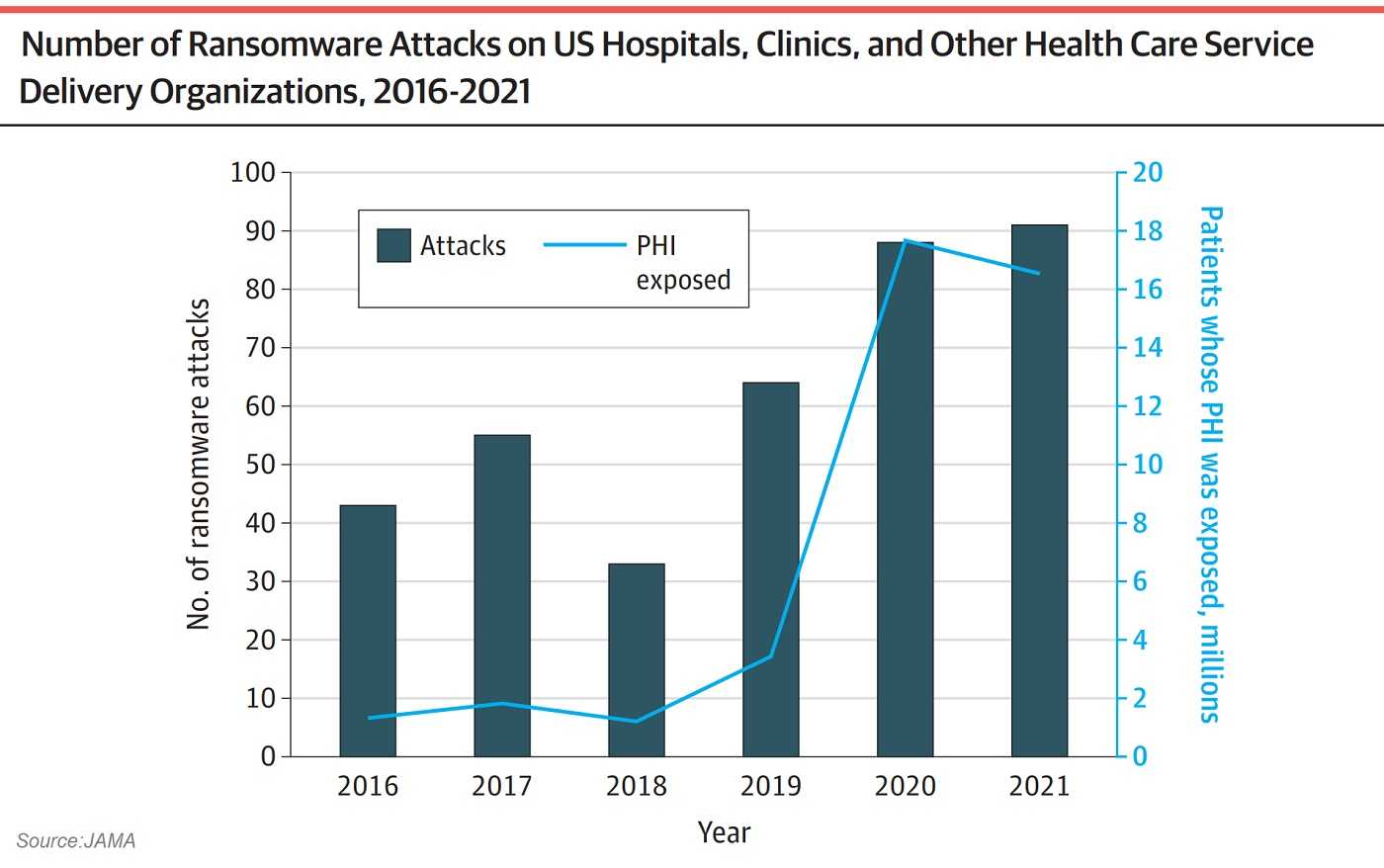
More findings show the annual number of ransomware attacks on the most targeted sector, healthcare delivery organizations (clinics, hospitals, dental practices, surgical centers, and others) more than doubled, from 43 to 91. Also, the amount of exposed PHI multiplied by more than 11, from 1.3 million in 2016 to over 16.5 million in 2021. JAMA finds the coronavirus pandemic helped fuel the trending increase in healthcare ransomware attacks.
Ransomware Threat to Patients
Healthcare ransomware attacks are costly for a few reasons. PHI and other important data get encrypted in the attack, and a ransom payment is demanded to get the information unlocked and returned. Paying the ransom, with some demanding payments in the millions of dollars, is the fastest way to get hijacked data returned and systems back-up and running. However, the FBI warns that ransom payments only encourage further attacks, and they strongly advise against it. In addition, just because the bad guy says they’ll send a decryption key, it doesn’t mean they will.
With provider care disrupted until patient PHI is returned, the cost of the ransom isn’t the only concern. While PHI is unavailable, patient treatment suffers, and lives can be at risk. Attackers count on this threat since it adds leverage for a quick ransom payment.
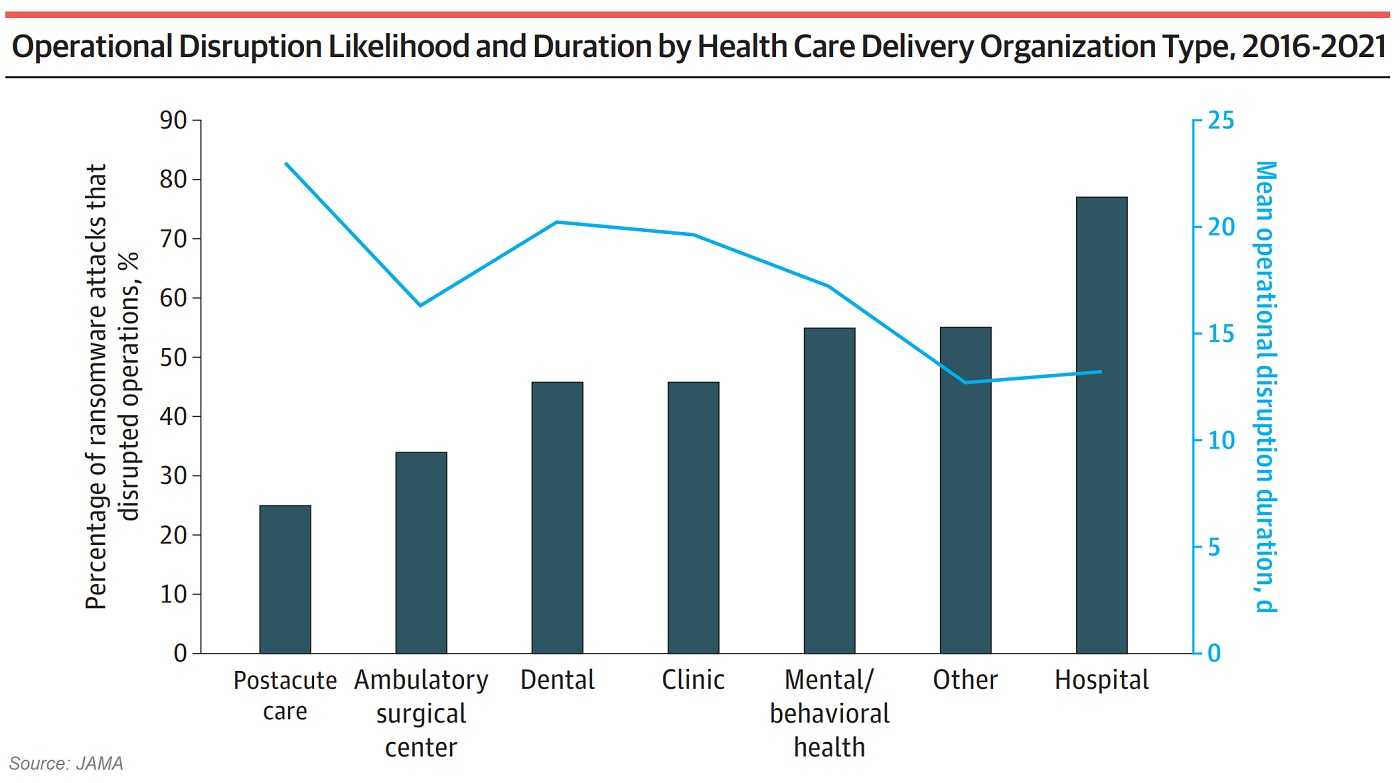
In addition to threatening the healthcare organization and the lives they care for, many cyber criminals post PHI to the dark web for sale; even if they do get a payment. It’s no surprise to discover these thieves aren’t always on the up and up. Should you find out that any organization in your healthcare system was the victim of a data breach or any type of cyber-attack, take action to limit your risk.
JAMA’s report also shows most ransomware attacks begin via phishing emails, saying “Research suggests that health care delivery organizations are very susceptible to phishing emails that deceive insiders into giving access to hackers, and such emails are a common entry point for ransomware attacks.”
While the future of healthcare ransomware attacks remains to be seen, there’s plenty of work to be done. JAMA finds “As policy makers craft legislation aimed at countering the threat of ransomware attacks across multiple industries, we urge them to focus on the specific needs of health care delivery organizations, for which operational disruptions may carry substantial implications for the quality and safety of patient care.”
In the meantime, you can help yourself by checking your Explanation of Benefit (EOB) statements as soon as you receive them. If anything looks amiss, contact your healthcare provider to make sure it wasn’t a billing error and if not, talk to your insurance provider.