Keeping a lookout for suspicious emails has become a daily consequence of our cyber lives. Phishing emails are notorious for having malicious attachments and opening them is a sure way to compromise your device and its data. These attachments are full of malware, ready and waiting to infect your system with a simple click. Make no mistake, any attachment in a questionable email can be dangerous. However, researchers at F-Secure found that some of this year’s biggest email spam campaigns used particular types of malicious attachments more than others.
.ZIP Attachment
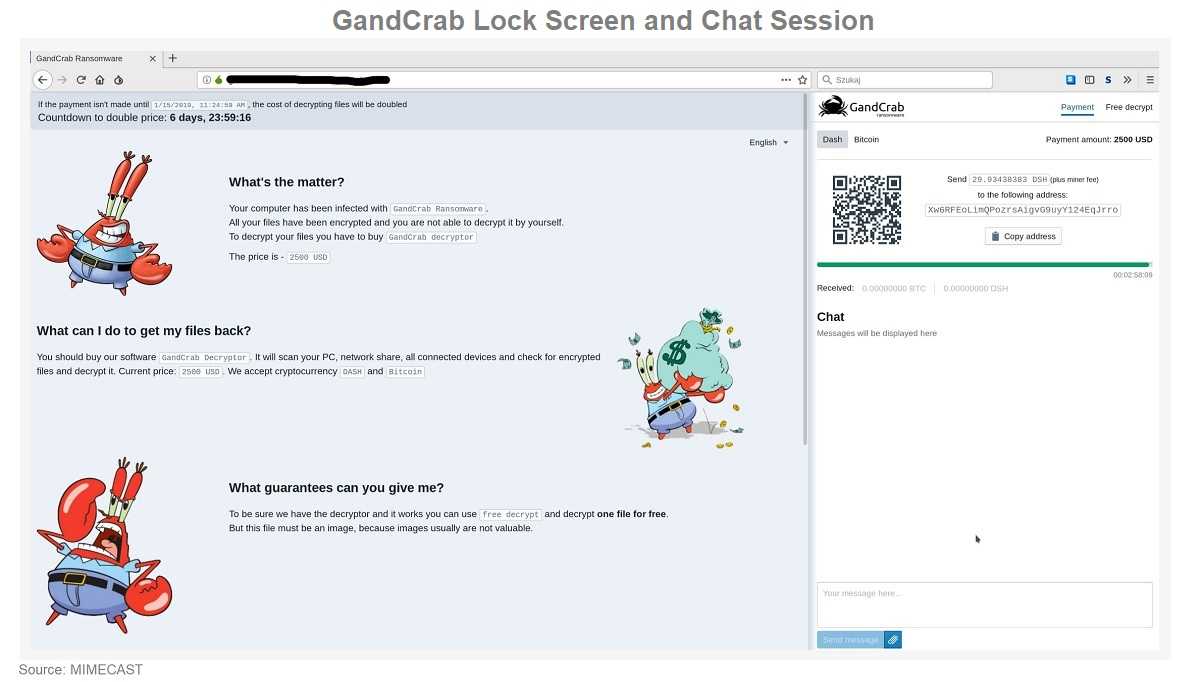
The most widely used way to compress many files into a single, easier way to attach and send are in zipped files. F-Secure found a huge spam campaign having ZIP attachments carrying GandCrab ransomware. The .zip attachment was disguised as a harmless photograph, but once opened the ransomware encrypts the device, rendering it useless. It also displays a ransom note demanding a payment from the user to de-encrypt the device.
.DOC/.XLSM Attachments
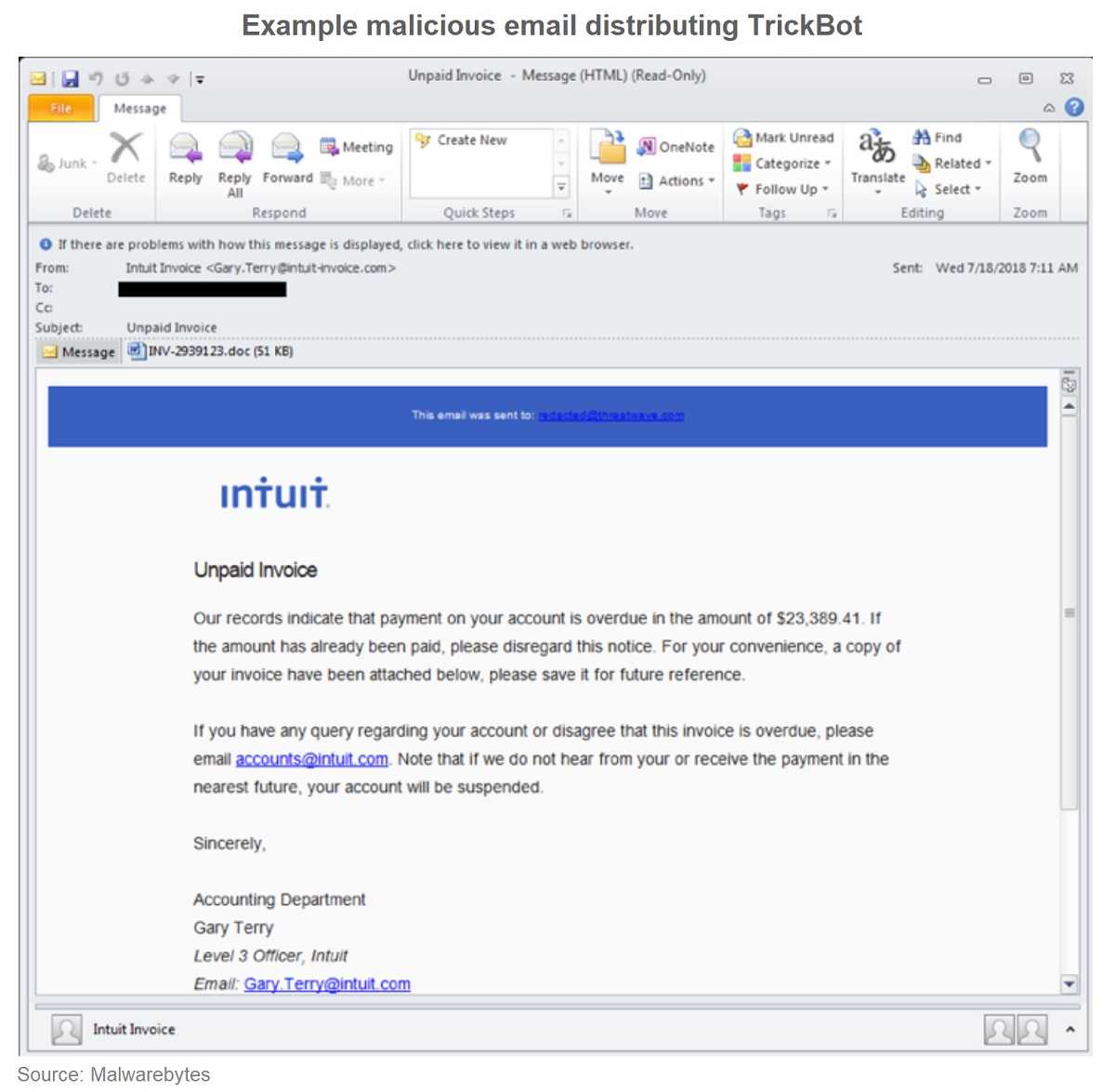
Both are Microsoft files widely used for business. DOC files often contain text, photos, graphs, and charts. XLSM attachments are used for sending spreadsheet files created with the Microsoft Office program. Both file extensions were largely used in a tax-themed spam campaign spreading the Trickbot banking Trojan. The latest version of Trickbot is very effective for stealing data from a device, in particular, financial data like banking and payment card information.
.PDF Attachment
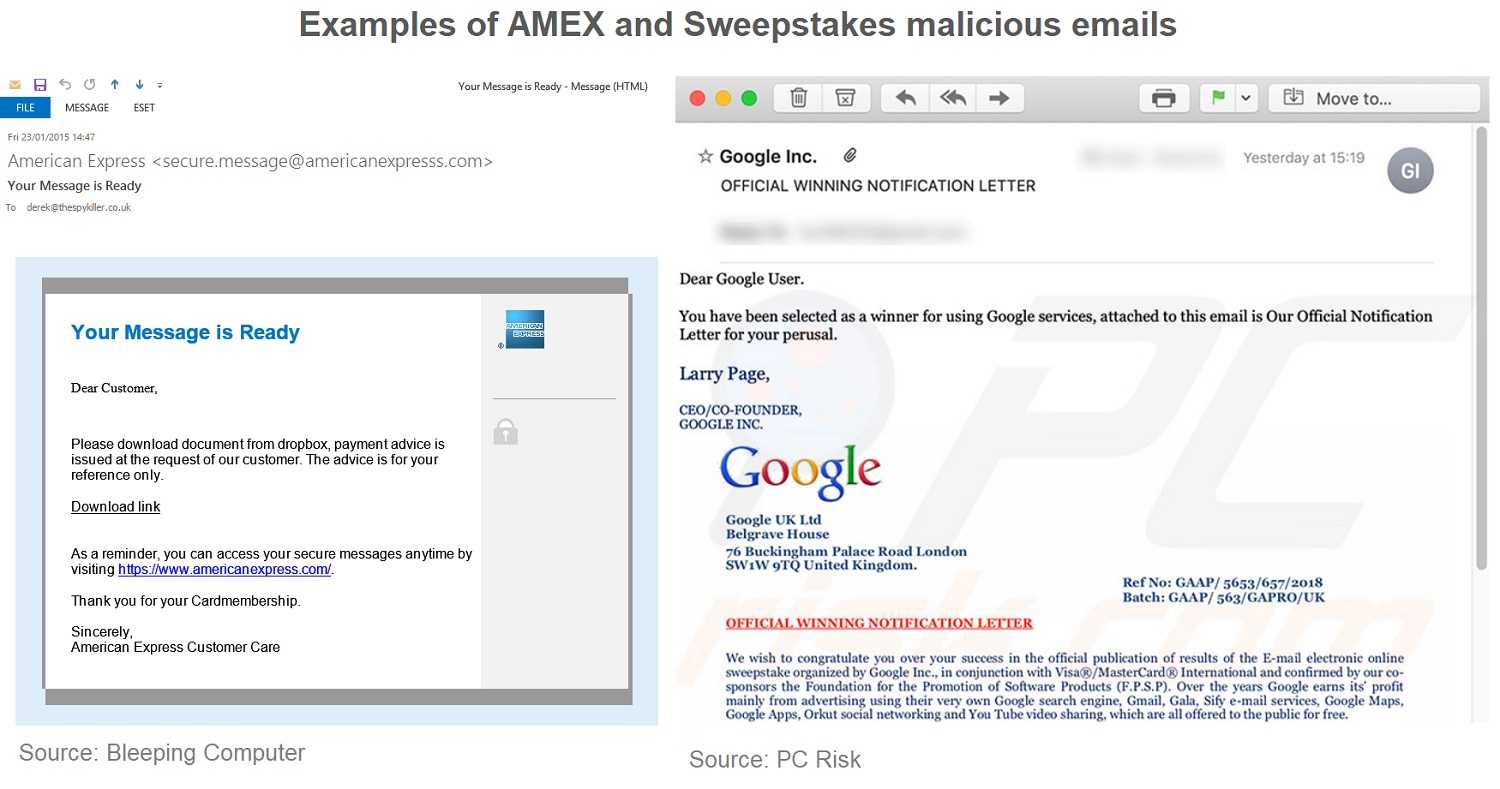
This extension stands for “portable document format.” These files are popular for the ease of opening, sharing, and printing files. The most popular tool for opening these is still Adobe Acrobat; though there are others. The two extensions were discovered being used for two phishing exploits. One used a ruse for AMEX customers and the other claimed recipients won an online sweepstakes.
.ISO and .IMG Attachments
.ISO files create a snapshot image of the data and layout of a CD or DVD and .IMG files store an image of raw disc data on a CD or DVD. Spam campaigns featured both extensions attached to the same email. They each held AgentTesla malware used for stealing victim information and credentials from browsers, emails, and other data in software that was already installed on a device. When opened, either file installed the AgentTesla malware.
 Despite the abundance of spam email attachments, common sense phishing tactics go a long way helping keep users safe. Always take a questionable email very seriously and keep in mind that no attachment can be considered "safe" anymore. If you don’t recognize the sender, don’t think twice about deleting it–especially if it contains links and/or attachments. Asking you to provide or verify account information is a huge red flag. To check if the request is for real, type in the URL for the company yourself, and not the one the email provides. That way you can verify if your account information is truly needed, especially for accounts dealing with information like financial account and payment card numbers as well as to supply passwords.
Despite the abundance of spam email attachments, common sense phishing tactics go a long way helping keep users safe. Always take a questionable email very seriously and keep in mind that no attachment can be considered "safe" anymore. If you don’t recognize the sender, don’t think twice about deleting it–especially if it contains links and/or attachments. Asking you to provide or verify account information is a huge red flag. To check if the request is for real, type in the URL for the company yourself, and not the one the email provides. That way you can verify if your account information is truly needed, especially for accounts dealing with information like financial account and payment card numbers as well as to supply passwords.