Shut The Door! Don't Leave Your Network Open To Account Takeovers
February 2, 2024
If your company is like most, it has seventeen sets of login credentials floating around online. According to a study by Arctic Wolf, those credentials exposed in data breaches or other cybercrimes are always welcome on the dark web. They’re typically for sale, but often offered for free, and anyone interested in using them has a digital buffet of login data at their disposal. Arctic Wolf’s report, 2020 Security Operations sheds light on account takeovers and how easily they can be launched. And like many cybercrimes these days, their rate of growth has exploded. In this instance, the number of corporate login credentials available on the dark web is up 429% from March to October of 2020.
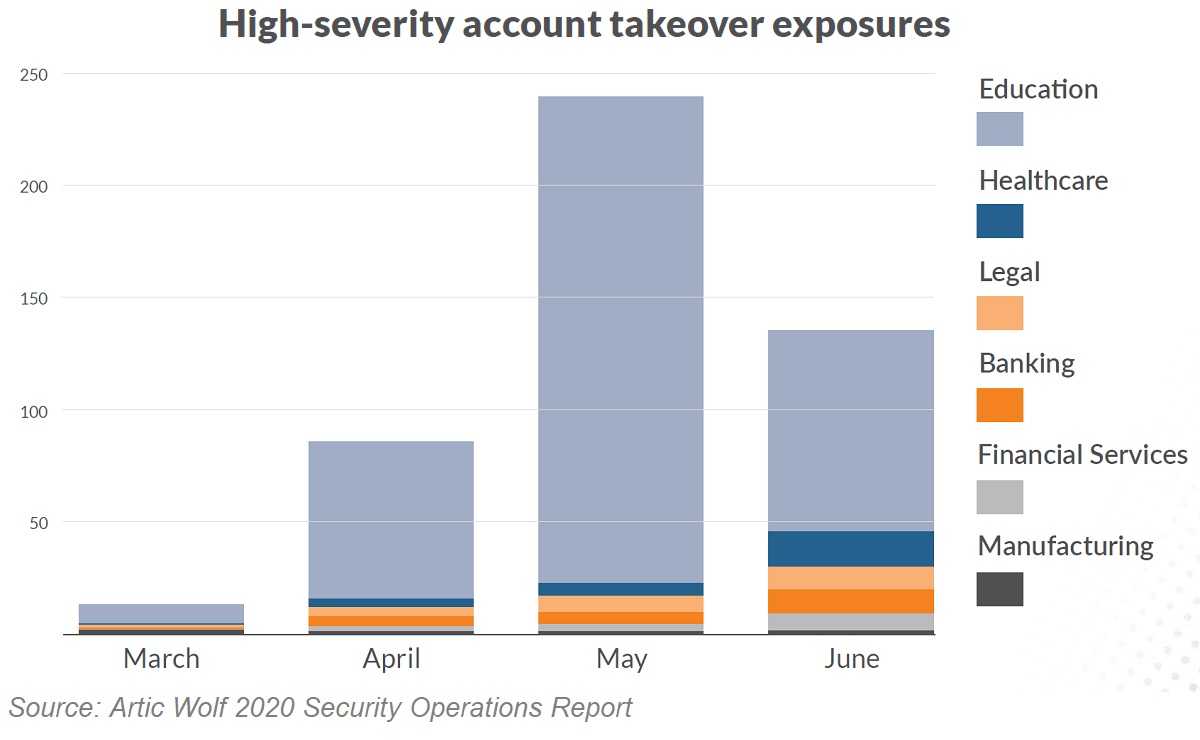
Account takeovers are something every enterprise should look to prevent; they’re considered a form of fraudulent crime. Overtaking just one account means any number of malicious attacks can be launched. When that happens, attackers can move around in a network and steal all kinds of confidential data and PII (personally identifiable information). Just one account takeover opens the door for ransomware, business email compromise, credential stuffing, brute-force, and other attacks that threaten organizations and individuals alike. Artic Wolf finds these and other hacking incidents take place mostly at night, when most IT departments have gone home. They also find high-risk security hacks happen between 8pm and 8am, and 14% happen on weekends when no one is watching.
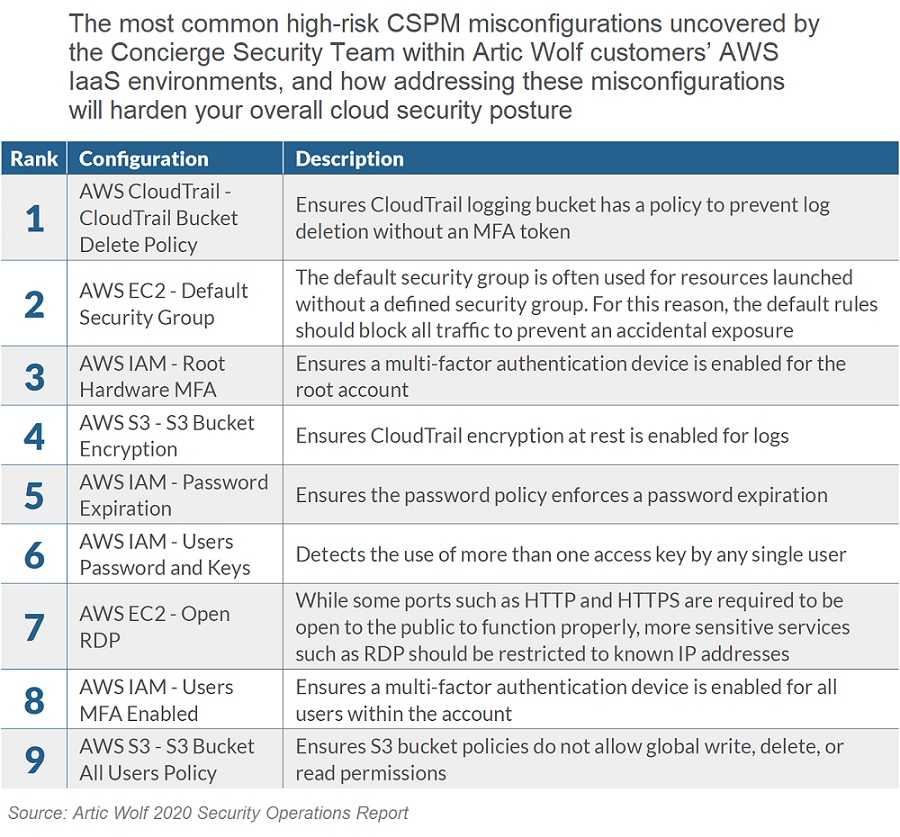
One important component allowing account takeovers is poorly guarded administrative rights. When too many employees have the keys to the kingdom, the opportunities for cybercriminals to enter, greatly increase. Hackers know poor password use is rampant, especially when passwords are reused. Third-party data breaches can expose this information and the organization is none-the-wiser. They may find out far too late that their login data is easily accessible on the dark web. According to LastPass, 91% of users know password reuse is incredibly risky, but 66% do it anyway—up 8% from 2018. That’s great news for cybercriminals, but disturbing news for the rest of us.
Shutting the Door on Account Takeovers
 Always use and/or require complex passwords, never to be reused for other accounts and change or ensure they are changed periodically.
Always use and/or require complex passwords, never to be reused for other accounts and change or ensure they are changed periodically.
- IT should limit the number of those with administrative access, especially at higher levels. Give those who need it just enough access to get their job done, and nothing more.
- Keep all software updated and apply patches as soon as possible, as they often fix security vulnerabilities.
- Regularly educate employees about account takeovers and other security risks: what they are and what they do, how to spot and prevent them, and what to do when a security issue is suspected.
- According to Arctic Wolf’s Mark Manglicmot “The only way to eliminate cybersecurity challenges like ransomware, account takeover attacks, and cloud misconfigurations is by embracing security operations capabilities that fully integrate people, processes, and technology.”