New York’s attorney general, Letitia James, announced that an investigation into credential stuffing had uncovered 1.1 million compromised customer accounts linked to 17 well-known companies.
Credential stuffing is a cyber-attack in which stolen user credentials – usually usernames (which could be email addresses) and corresponding passwords – are used with brute force to make automated login requests. The stolen user credentials are typically from data breaches that could have happened recently, but also may have occurred long ago. These types of attacks are particularly effective when the same username and password combination is used across multiple websites or services.
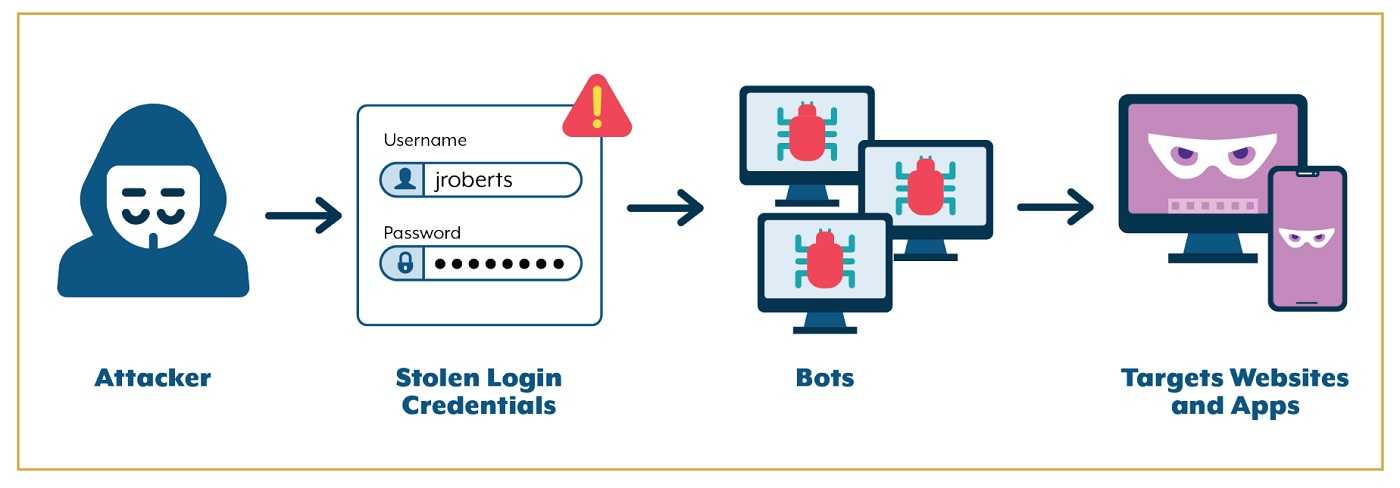
To avoid becoming a victim of credential stuffing and other password-related attacks, it is recommended that you use a strong and unique password on your email account, as well as for every account you use online. It also limits the number of passwords you have to change if one of your accounts is involved in a data breach. Strong passwords, such as those using a combination of upper- and lower-case letters, number, and special characters and that are not easy to guess help to defend against password guessing and brute force attacks like this.
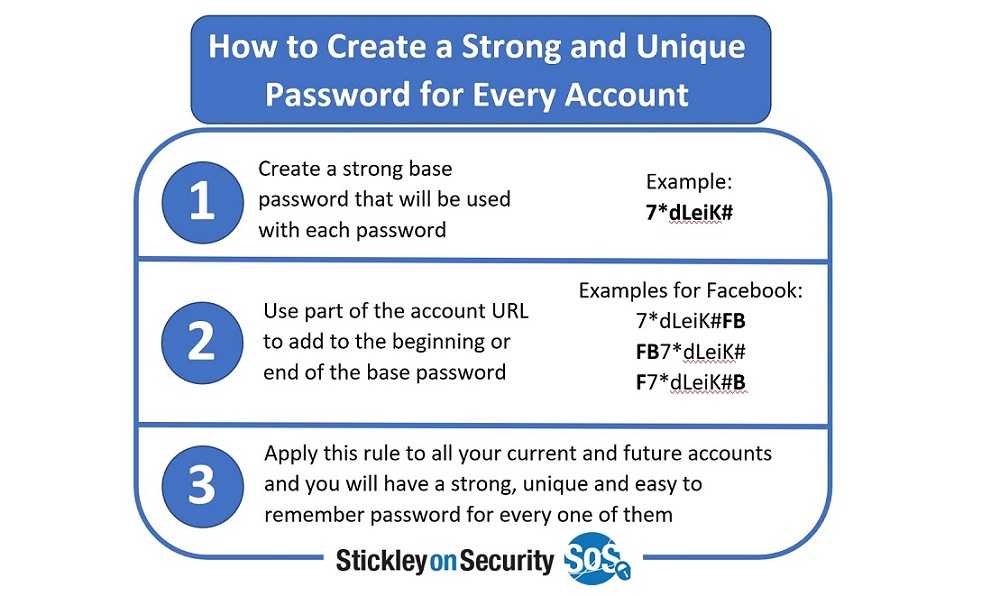
Because we are all pretty tired of having to remember so many passwords, you may need some guidance on remembering them all. You could write down clues for the sites to jog your memory. You could also use a password creation strategy that is consistent. For example, Jim Stickley of Stickley on Security suggests using the website name to create a password. You start with a base password of at least six characters and add characters from the website to it. Your base could be “XU5mh” and you might have an account at Google. Your password could be “XU5mhGo,” using the first two letters of the site. This will prevent them from being duplicated, for the most part.
Another option to help you is to use a password manager. There are many options from apps to websites. Just remember that if your master password for one of those sites gets stolen, or if the password manager company is breached, you will need to change ALL of your passwords.
Finally, turning on two-factor authentication (2FA), also known as two-step verification (2SV), or multi-factor authentication (MFA) adds an extra layer of protection that may stop a credential stuffing attack in its tracks. If this is offered for an account, no matter how unimportant you think the website may be, activate this feature.
The Attorney General’s Office of New York State created a Business Guide for Credential Stuffing Attacks. In it, there was reference to a study by Digital Shadows that there are 15 billion stolen credentials making their way around the Internet. It also noted a Ponemon Institute finding that businesses lose an average of $6 million per year to credential stuffing attacks.