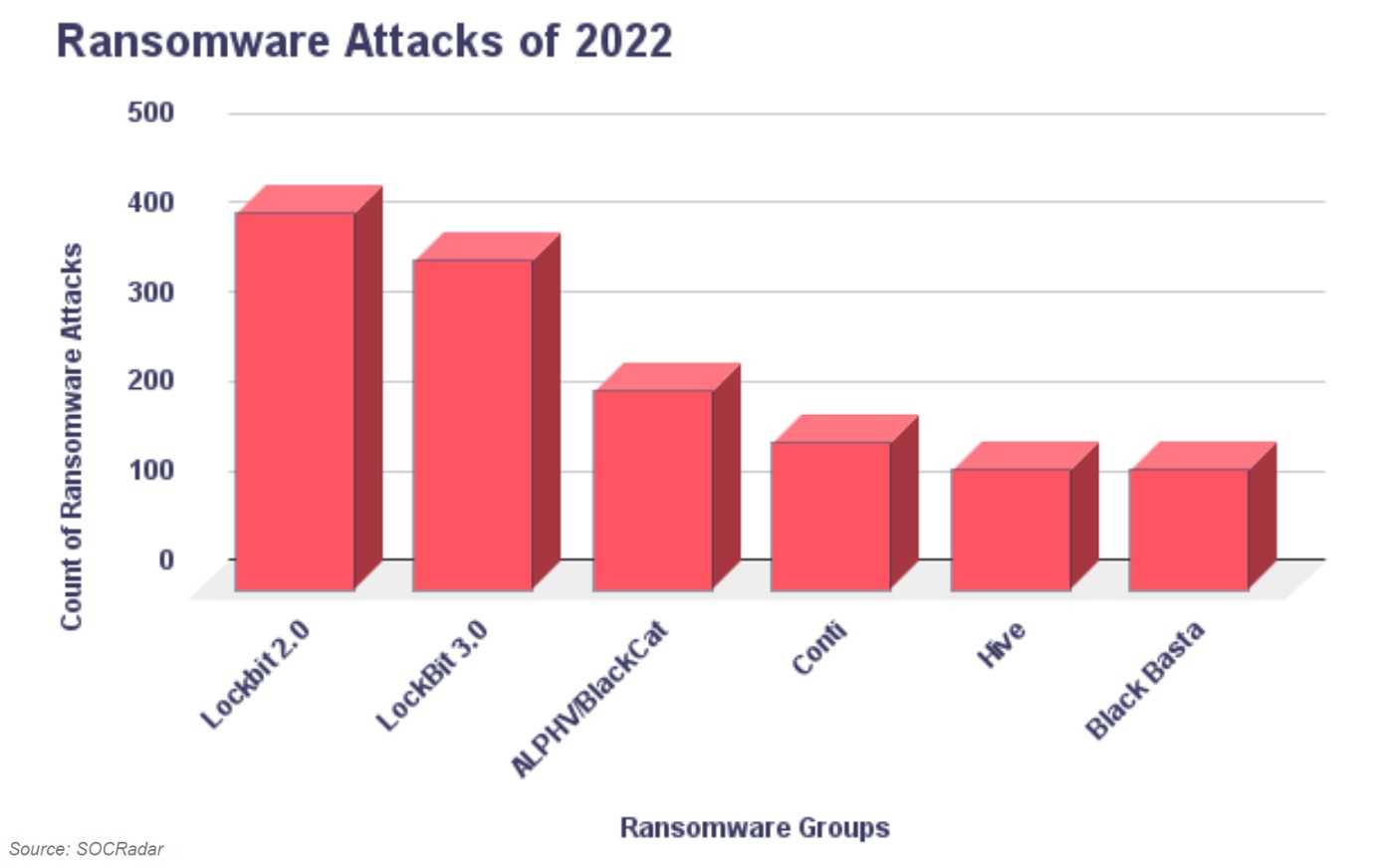
According to FBI information, Hive ransomware actors had been highly active in the recent past. As of November 2022, they had managed to attack more than 1,300 companies worldwide and receive approximately $100 million as a part of ransom payments. As a result, the HHS, CISA, and FBI came together to issue a joint announcement to warn businesses of the Hive activity; and then they stopped them and prevented many organizations from being victims by taking the hacking group down.
The announcement mentioned that the Hive actors (a ransomware-as-a-service group) use a unique ransomware that allow developers to not only develop the malware, but also maintain and update it from time to time.
The attacks of note primarily took place between June 2021 through at least November 2022 where the threat actors used ransomware to attack a wide range of infrastructure sectors and different businesses. Some of the most critical infrastructure sectors included Information Technology, Critical Manufacturing, Healthcare, and Public Health, Communications, and Government Facilities.
Well, there is some good news to report after this. FBI have since announced they, along with international law enforcement agencies, were able to hack the group, break into their systems, and steal the digital keys the hacking group used to unlock their victims’ data after locking them up. This meant that the victims were not obligated to pay up. The FBI warned them in advance, or in the case of a school district and a hospital, the agency provided them the decryption keys.
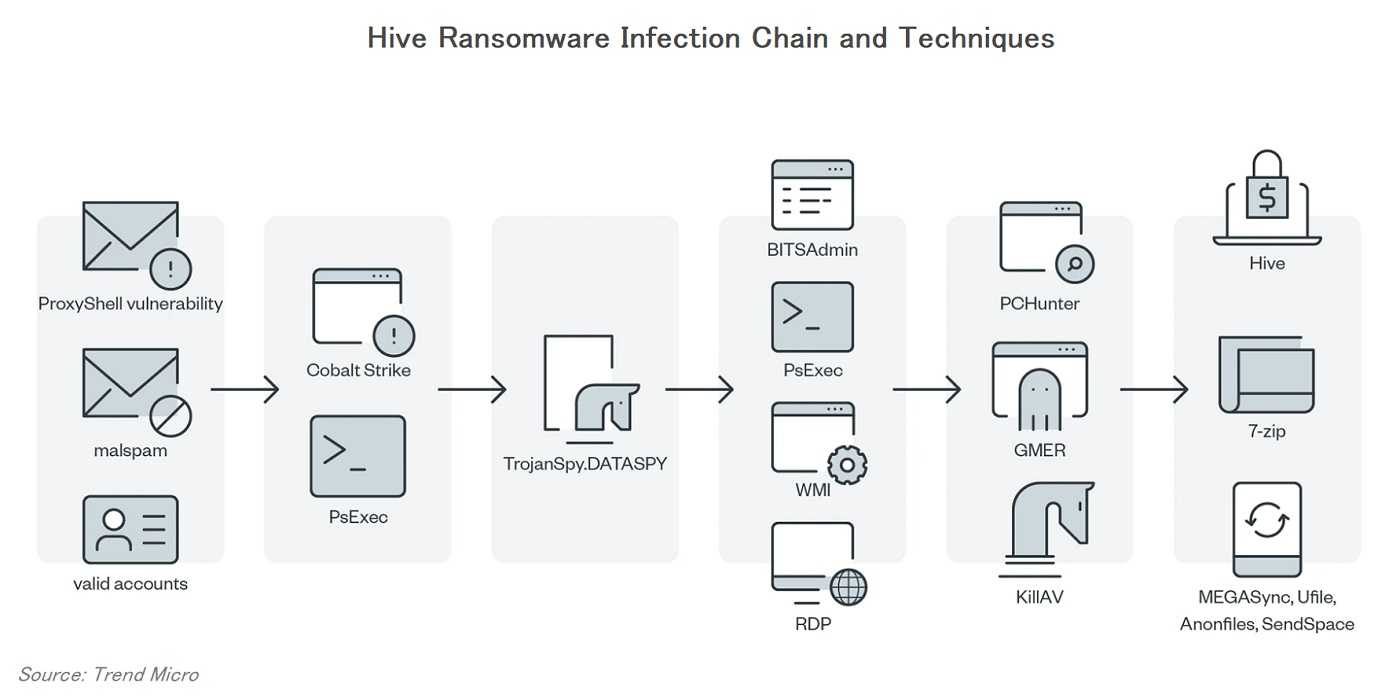
In the announcement at the end of 2022, Hive actors began using single-factor logins with the help of virtual private networks (VPNs), Remote Desktop Protocol (RDP), and other types of remote network connection protocols to get access to the victim’s networks. They used that information to get access to multifactor authentication and enter FortiOS servers of many business accounts. When they enter these servers, they get access to critical business information without requiring a second authentication factor. Once access is gained, they identified the backup-related processes, antivirus information, terminate the volume copy shadow services, and even delete Windows events logs, especially the System, Security, and Application logs. They used such strategies to target more than 1,500 victims globally, according to the FBI.
While the threat from Hive is off the table for the time being, there are many other similar groups performing similar attacks. It remains important to perform regular backups of critical information, keep them off the network, and make sure they are working so they are ready if they are ever needed. In addition, make sure all employees know the signs of phishing. Generally, that is how ransomware makes its way into the network in the first place.
Whenever hacking groups are taken down, it’s good news. It’s also worth noting that they are unlikely to just go away. In fact, they have options. They may regroup under a different identity or the members may go join other groups. Sadly, the individuals were not identified in this and rarely are. So, even though law enforcement deserves kudos, it doesn’t make the threats go away. However, there is one less such cybersecurity threat…for now.