Why settle for minnows when whales make much bigger, better targets? That’s a question hackers might ask themselves when determining their next victim. With no shortage of information available online about C-Suite and other high-level executives, they make lucrative email phishing targets. These execs are known as “whales” and bad actors love reeling them in because it pays big time.
Whales make the most lucrative phishing targets within an organization because they often have access to company funds and can make wire transfers happen quickly with few to no questions. It’s no surprise these execs have become a gold standard for phishing, fraud, and profits.
Big Whale, Big Phish
The cost of big whaling reached $12.5 billion last year, according to the FBI. The amount stolen is set by the hacker and some are greedier than others. For example, a Snapchat HR employee handed over valuable payroll data including employee personally identifiable information (PII), W-2 forms, and stock option details. Another attack began with a new CEO at Mattel, a staffer eager to make the new CEO happy, and ended with a $3 million wire transfer to a bank in China.
There’s no doubt criminals do their homework before an attack. Social media posts, work-related websites like LinkedIn, and a company website can all offer details on employees that are needed for whaling. Knowing who the whales are and the staffers whose job facilitates moving funds, all provide the perfect setup. Also, hackers use company logos, signatures, and more in their email, making it look legitimate and unsuspecting. But sometimes, a hacker may be after more than money alone.
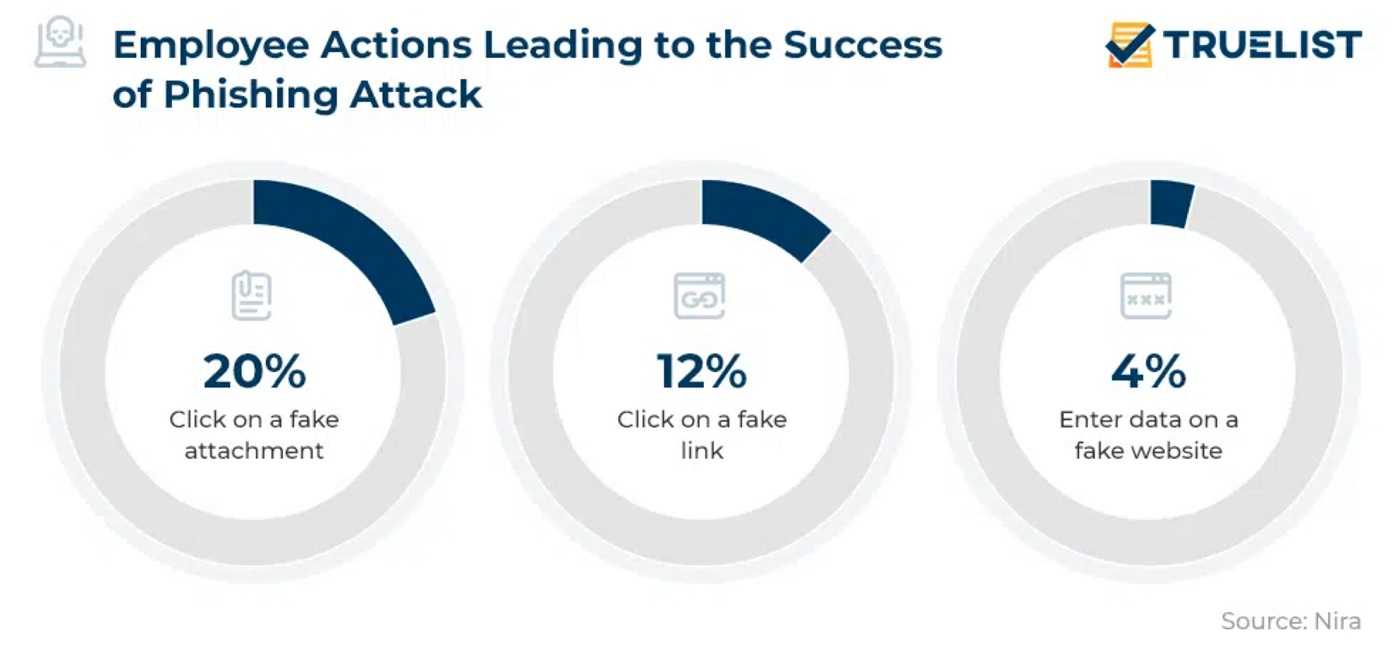
When Whaling is Just the Start
A whaling attack can be the beginning of a larger criminal plan. A successful attack shows the hacker that a targeted company may be ripe for much bigger picking. Ineffective system security and lax (or non-existent) data security policies, including those having to do with wire transfers, can give hackers a green light for further attacks. Also, they can initiate a whaling attack as beginning leverage for much bigger plans. All these circumstances can lead to massive data theft, malware infections, and further cybercrimes including devastating ransomware attacks.
Keeping cybercriminals from a profitable whaling attack involves a company stepping up their security procedures, starting with employee cyber-education. It involves educating ALL employees, including the whales, on the do’s and don’ts of online security. An employee who knows what email phishing looks like can stop a whaling attack before it starts, and any whale would be happy about that.
Look out for these signs:
 An unexpected link or attachment from the sender or a sender that is unknown
An unexpected link or attachment from the sender or a sender that is unknown
- Improper grammar, spelling, or other language errors
- A threat that something bad will happen if you don’t perform an action quickly
- A sudden request to change wiring or banking instructions
Of course, there are other clues that someone is casting a big line, but these are tell-tale signs and should always be independently verified to be legitimate.