Spear phishing attacks by a notorious Russian-backed threat group were launched against a large U.S. car manufacturer, who is currently unnamed. The group known as FIN7 used the highly targeted phishing campaign to attack IT department employees and others with top levels of system access.
The Russian cybercrime syndicate FIN7, aka Carbanak, came to prominence in 2015. The threat group is also known for ransomware attacks against the gambling and hospitality industries. In this latest attack, FIN7 directly targeted IT employees and those in upper levels of the company, often referred to as “whales.”
FIN7 used typosquatting, aka URL hijacking, a type of social engineering attack. Threat actors create a fake URL, often with a slight change in spelling from the legitimate website that goes unnoticed. The bogus, malicious website is used for fraud, or in the case of the car manufacturer, spreading malware.
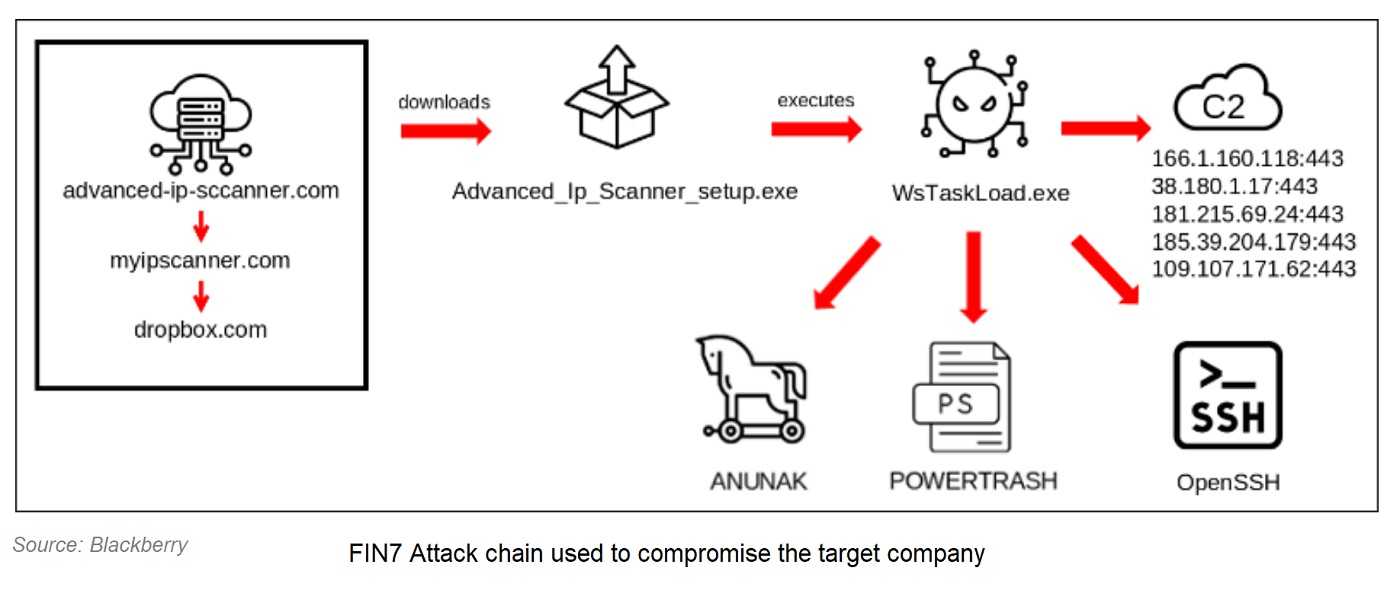
The group also used socially engineered phishing tactics that can target victims by name, title, and other PII to lure the victims to click on a typosquatting website. Just one click downloads malware, which is especially dangerous when a device is connected to a corporate network. Having that network access gave FIN7 the ability to compromise the car manufacturer’s security and run amok in its system.
Safety First
 Lessons to learn from FIN7’s attack is that no employee is immune from being targeted, especially those from management to C-suite. Even though we tend to think phishing attacks target lower-level employees, which they do, the reality is every level staff is fair game. That’s especially true since attacks against upper-level personnel offer attackers higher levels of system access.
Lessons to learn from FIN7’s attack is that no employee is immune from being targeted, especially those from management to C-suite. Even though we tend to think phishing attacks target lower-level employees, which they do, the reality is every level staff is fair game. That’s especially true since attacks against upper-level personnel offer attackers higher levels of system access.
For things we can control, red-flagging socially engineered attacks, or those using personal information to lure us, is something we should all be aware of. These attacks can use our job and title, and also arrive in our personal email accounts. They often use lures like urgency and other ways of prompting a quick response.
Using fake URLs (typosquatting) is another trick up a hacker’s sleeve. They know we rarely, if ever, check a URL spelling. Thanks to that, hackers sneak in a slightly different spelling that often goes unnoticed and brings you to their fake website. So, always carefully check the URL spelling more than once because our eyes can deceive us.
Keep PII Under the Hood
Oversharing information on social media and networking websites is still a nail in the tire. Limit the information you post on these websites. On business-related sites such as LinkedIn, use general terminology to describe your duties, rather than titles or other specifics.
Taking a bit of time to learn how to identify phishing and taking care of what you put on the internet can help to keep the air in your tires.