$1.8 Billion Cost For Businesses Hit With BEC, More $$ Than Ransomware Attacks
By: Jim Stickley and Tina Davis
August 25, 2022
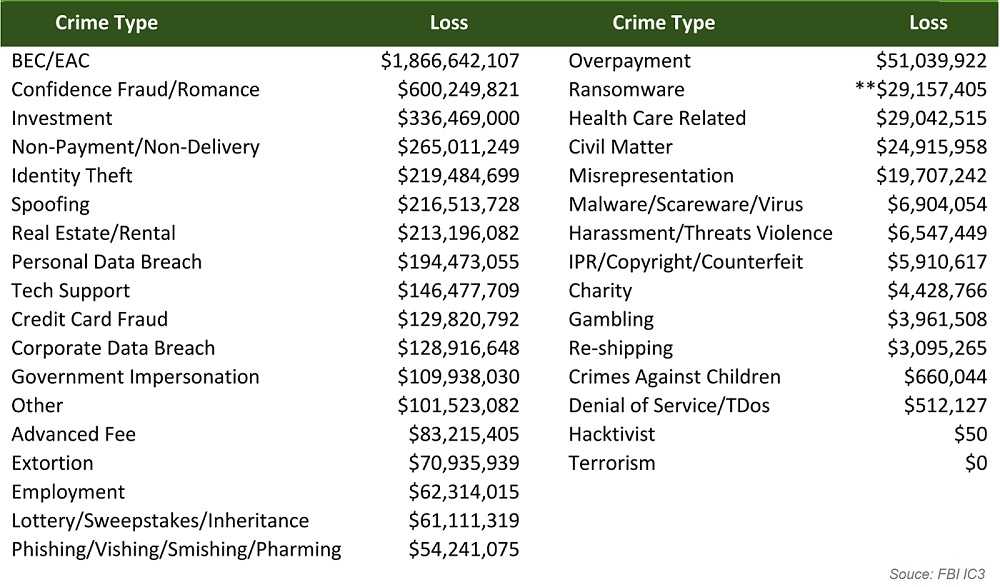
Business Email Compromise (BEC) attacks cost businesses more than $1.8 billion in damages last year, according to an FBI report. It’s believed an additional $300 million in fraud can be added to the BEC total. The FBI’s “Internet Crime Report 2020” sheds light on BEC attacks which added up to more than the combined cost of ransomware crimes last year. Taking a closer look at BEC’s show how they work and how to help avoid them.
BEC’s and Socially Engineered Phishing Emails
A BEC typically starts with socially engineered email phishing attacks. Social engineering gathers tidbits of information about employees, especially from social media posts and company websites. In particular, hackers look for those employees involved with making wire transfers or have access to funds. Using the gathered information makes the email much more likely to be opened, trusted, and acted upon. It’s very difficult to stop a BEC attack once it’s in motion.
BEC emails typically request large wire transfers be made to a vendor or another trusted source, and most rely on a sense of urgency for the transfer. The email recipient is pushed to make the funds transfer quickly which can lead to short-cuts in security procedures. The scammer provides an account to send the funds to, which in reality is their own account and it disappears once the funds transfer is made.
BEC: What to Do, What Not to Do
- Look for grammatical errors, bad spelling, or odd phrasing in emails. English may not be the hacker’s primary language, or grammar and spelling is not their strong point
- Be especially aware of any language using urgency or other pressure to get the target employee to act quickly and possibly circumvent wire transfer security protocols. Urgency should be a sign to slow down and be especially careful
- Use multifactor authentication (MFA) or 2FA (two-factor authentication) to help protect email and other accounts from being used for BEC and other cybercrimes
- Always confirm a wire transfer, including any change in account number, with at least one other employee. Never use contact information provided in the email – it could be a setup by the hacker. Look it up yourself using a trusted source
- Don’t overshare on company and personal social media. Details are what bad actors look for.
Remember, a CEO or any executive would always prefer being asked to verify a large wire transfer rather than pay for BEC fraud. Don’t be afraid to ask them first.