As is said, the bigger they are, the harder they fall. When it comes to cybersecurity, that’s especially true for executives and C-Level members of an organization. Trend Micro discovered a highly effective spear phishing email campaign using a fake Office 365 email message as bait. The hacking scheme targeted high-level executives and board members in six countries. Those include the U.S., UK and Canada, with the U.S. executives overwhelmingly the most targeted of all.
A calculated reason for aiming at executives is the belief that those in high places may lack the cybersecurity skills to assess if an email or other lure is legitimate or not. Another reason is that these high-level targets know and have access to the most sensitive information a company has, including finances. The success of this phishing campaign shows that for the most part, the hackers were correct in their assumptions.

Cyberattacks against a company CEO and other executives is also called “whaling” referring to high-level targets as opposed to lower-level staffers (the phish). While mainstream employees are a small-phish target, they are also more likely to be cyber-savvy about phishing emails than those in high places. For whatever reasons, executives may be more removed from cybersecurity awareness, and cybercriminals are ready to take advantage of that.
The success of the Office 365 hack proved there’s a security disconnect for those higher up in the food chain. It’s the fourth iteration of the bogus Office 365 email attacks, and with every version comes improved tactics that result in a higher level of success. Aside from the fake Office 365 emails, clicking a link in the text takes a target to an “official” website designed to steal as much PII (personally identifiable information) as possible. Information needed to carry out these socially engineered attacks is for sale in underground forums, pricing C-level credentials from $250 to $500.
The information for these attacks isn’t limited to underground forums. Beyond buying email addresses, hackers also scour social media sites for PII about whales and other employees. Sites like LinkedIn, company websites, and other social media platforms are just a few sources for PII. If data security is a goal for an organization, sharing and over-sharing PII online is definitely not the way to do it, no matter what your job title is.
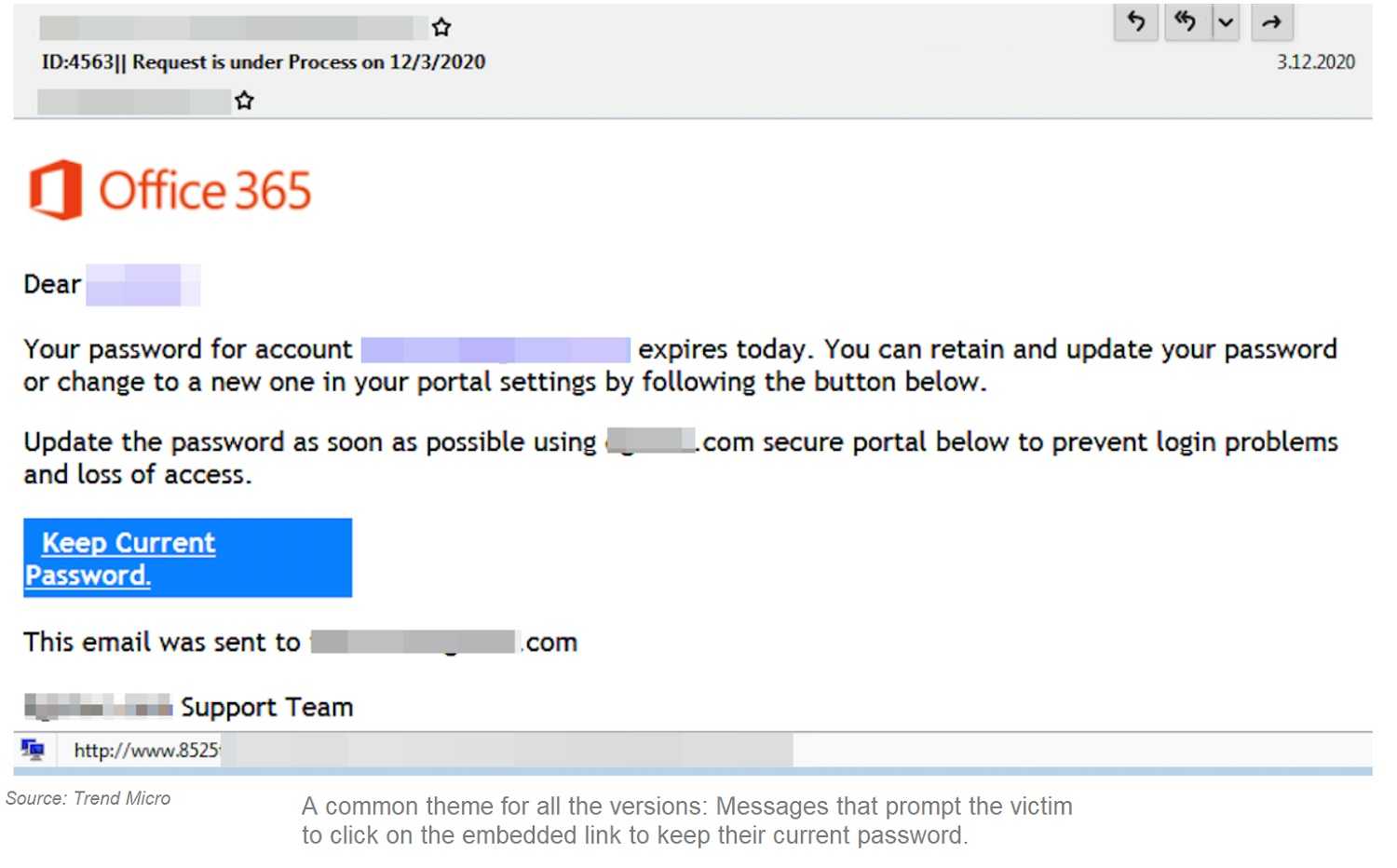
If a fake Office 365 email can be this effective on a corporate Big Phish, there’s a need for cybersecurity education and awareness for all levels of staffers. Cyber-education should be ongoing, as email phishing and other attacks improve and trend over time. Find a way that makes sense in your organization. Many options are available including delegating an employee to provide awareness training. There are also cybersecurity professionals that will bring training onsite to your organization. If those don’t suit the need, there are companies that provide ongoing education programs online.
Posting too much PII on any website is never a good idea, especially since we know hackers are actively searching for it to start a targeted attack. Keep the details as general as possible, particularly if the role is in human resources or finance—the employees with a lot of access to PII and the company financial information and accounts. Remember, the guideline for any employee posting PII is always “less is more secure.”