We have all heard the term “phishing,” possibly even ad nauseam. Most of us even may immediately know what to do to avoid becoming a victim. However, according to Forbes some victims of phishing are actually those in high-level financial-related positions at companies, such as the CFOs to the tune of $12 billion. This is since 2013 and includes those in the U.S., the UK, and in Europe in over 78,500 firms.
Phishing at that level is often referred to as whaling—as in catching the bigger phish. Often these messages appear to come from a CEO or other boss. The text itself often reads familiarly to the reader, but also has some type of urgency built into it. That is completely intentional by the criminals to make the recipient feel as if there isn’t enough time to think about any included requests in hopes they will just react and wire funds.
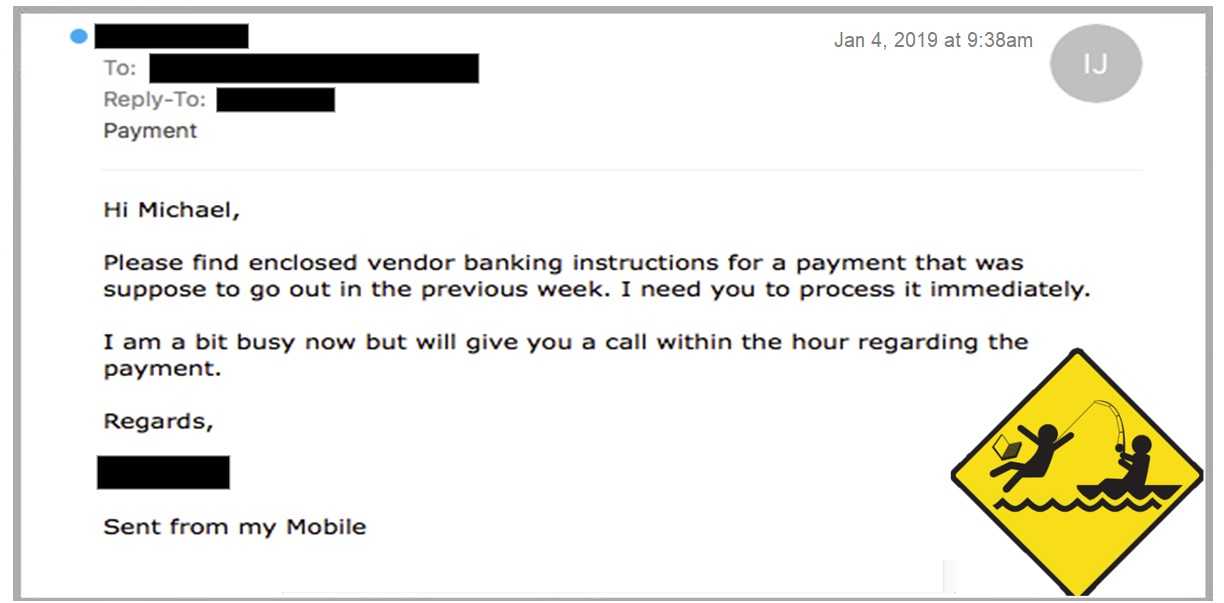
Most of the time it is indeed a wire transfer that is requested in this phony message.
The most vulnerable in this type of scam are organizations that don’t have dual-signatory requirements for transfers. Having lax or no cybersecurity standards also put the organization in the higher likelihood of becoming a victim of whaling schemes.
Before you dismiss anything and say “Hey, we have dual-signatory requirements for amounts over $xxxx.xx,” the criminals are on to that too. They often know what those limits are, or are close to, and will very cleverly ask for amounts just under them.
 Always have another person approve wire-transfers, even if it’s a small amount. If there is a sense of urgency in any message asking for funds to be sent anywhere, just verify the request. Odds are, if it comes at 3am, it likely can wait till you get to the office. If it REALLY is that important, the CEO will most likely call you asking for the funds rather than relying on an email message and one must wonder why he or she would be asking in that manner anyway.
Always have another person approve wire-transfers, even if it’s a small amount. If there is a sense of urgency in any message asking for funds to be sent anywhere, just verify the request. Odds are, if it comes at 3am, it likely can wait till you get to the office. If it REALLY is that important, the CEO will most likely call you asking for the funds rather than relying on an email message and one must wonder why he or she would be asking in that manner anyway.
Some security experts recommend cybersecurity insurance to protect against this as well as other risks such as ransomware and extortion (or sextortion). Both of the latter are on the rise and used in conjunction with whaling, it can be a rather effective campaign for the criminals.
 Training and awareness will continue to be the best defense to prevent all types of phishing, whether it’s whaling, smishing (text phishing), vishing (voice phishing), or run of the mill mass spam campaign phishing for the low-hanging fruit.
Training and awareness will continue to be the best defense to prevent all types of phishing, whether it’s whaling, smishing (text phishing), vishing (voice phishing), or run of the mill mass spam campaign phishing for the low-hanging fruit.
Small businesses have the most to lose if phishing leads to a serious data breach. Statistics have shown that 66% of these do indeed shut down for at least some period of time after such an incident. Per the U.S. National Cyber Security Alliance, 60% of small businesses are unsustainable six months after an attack. Damage can be up to $690,000 for mitigation for SMBs while larger organizations can often weather the storm, though not without some amount of damage.
The U.S. feels 50% of these whaling attacks. Until SMBs start taking cybersecurity strategy and training seriously, these threats will continue. Prevention is always the best defense.