Home Router Flaw May Allow A Home Network Takeover
March 16, 2023
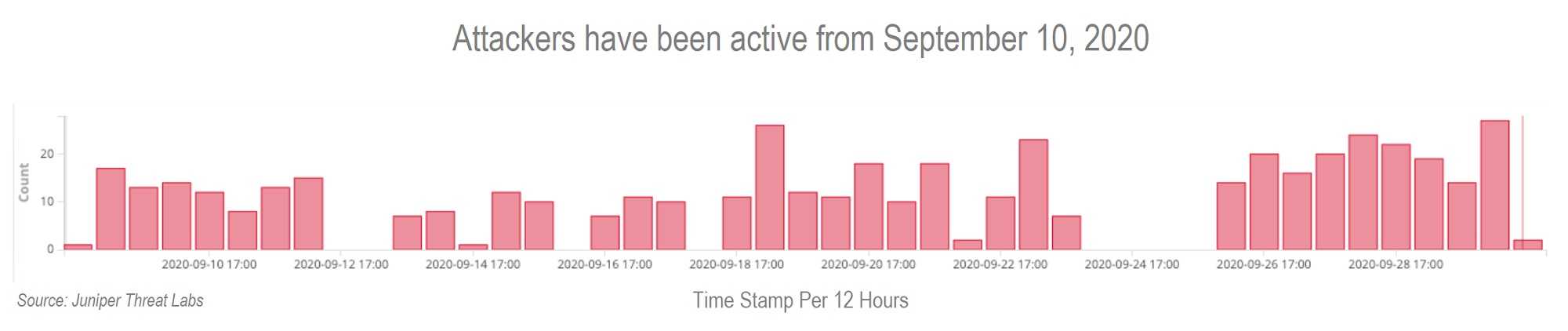
It’s once again a time when routers are targeted…successfully…by attackers who can take them over and wreak havoc in the universe. Maybe it’s not so far-reaching as to make it to into space, but it most certainly is on this planet right now. Some up to no good, have discovered they can take advantage of a vulnerability in home routers that use Arcadyan firmware. According to Juniper Threat Labs researchers, it is being actively exploited utilizing the Mirai botnet at this very moment.
The list of affected routers is rather extensive and covers a lot of different vendors including Verizon, British Telecom, Orange, and Vodafone, as well as many more. It’s likely the total number of affected devices runs far into the millions. The issue was discovered a while ago and the company, Tenable published an advisory about it way back in April. They just recently added proof of concept code for it. But like some other recently discovered flaws, such as the recent printer flaw affecting HP printers from 16 years ago, now that the word is out, it’s likely to be used against us more.
Some of the affected models include:
- ASUS DSL-AC88U (Arc VRV9517)
- ASUS DSL-AC87VG (Arc VRV9510)
- ASUS DSL-AC3100
- ASUS DSL-AC68VG
- HughesNet HT2000W
- Telus WiFi Hug (PRV65B444A-S-TS)
- Telus NH20A
- Verizon Fios G3100
The exploit was tested on a Buffalo model router (there are several of this brand affected too), but it’s suspected--and perhaps should be assumed--it affects all devices running Arcadyan firmware. This is being tracked under CVE-2021-20090. If the attackers find an unpatched router, they could bypass authentication and deploy the botnet.
 Hardware needs updates, just like your operating system does. So, it’s important to keep on top of these and apply any patches as soon as they are made available to you. Go directly to the manufacturer’s website to determine if you have an affected product and follow the instructions on updating your devices. It’s also imperative to check for updates as soon as a new device is ever installed on your home network. These items can sit on store shelves for a very long time before they make it to you, so they often do have some updates waiting when you install them. And whatever you do, change the default password first.
Hardware needs updates, just like your operating system does. So, it’s important to keep on top of these and apply any patches as soon as they are made available to you. Go directly to the manufacturer’s website to determine if you have an affected product and follow the instructions on updating your devices. It’s also imperative to check for updates as soon as a new device is ever installed on your home network. These items can sit on store shelves for a very long time before they make it to you, so they often do have some updates waiting when you install them. And whatever you do, change the default password first.